When it comes to types of proxies, there is no one-size-fits-all. The types of proxy servers can be classified based on location, traffic flow, anonymity level, application, service, and type of IP. It all depends on your custom and dedicated demands.
A proxy server is simply, the middle man— the intermediary that integrates and adapts all traffic requests and responses coming and going to another network (like the Internet). These requests are usually coming from clients requesting resources, from HTTP, FTP, DNS, or other services, usually located on other networks. The proxy adds structure to these incoming or outgoing requests (responses) coming from distributed networks.

A proxy can be anything from a piece of software that runs on a desktop to an appliance protecting traffic on a datacenter. Today, there are many types of proxy servers out there, but the most popular is the Web Proxy, which facilitates the access to the WWW, and provides IP anonymity, flow control, and reliability.
This is a guide to proxy types. Here you’ll learn everything you need to know about the types of proxies, what they are, and what they can be used for.
Mục lục.
- Types of Proxies Based on Location.
- Types Proxy Based on Traffic Flow.
- Types of Proxy Servers Based on Anonymity Level.
- Types of Proxy Servers Based on Application (and protocol).
- Types of Proxies Based on Service.
- Proxy Types Based on IP.
1. Types of Proxy Based on Location.
The initial idea of a proxy server was to centralize requests and responses to simplify complex distributed networks. In a distributed network all the nodes can impact the overall performance of the network (look at the diagram below). But in a hub-and-spoke or centralized network, the core node influences other nodes.
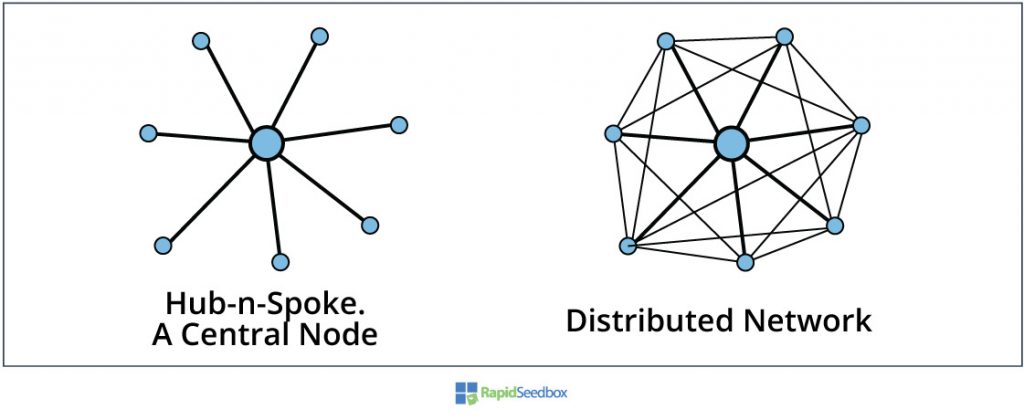
So regardless, if you place a proxy in an internal network separating two subnetworks, or if you place it between a private and public network, aka, (the Internet), the idea of the proxy is still to centralize requests and responses. This idea leads us to two types of proxies.
a. Public-facing Proxy.
Also known as the Internet-facing proxy. This is the most popular anonymizer of web browsing, Internet-usage limiting, and other Internet-facing activities. This proxy is located on the boundary of a private (internal) network and the Internet. An example is the internet firewall, which acts as a proxy for two types of traffic: inbound and outbound. Another example of a public-facing proxy is your Internet gateway.
b. Private-to-private Proxy.
This proxy separates an already complex private distributed network, usually a WAN or campus network. This type of proxy adds structure and improves security in an internal network.
2. Types of Proxy Based on Traffic Flow.
Another classification regarding location can be made based on the direction of traffic. Just like a firewall filters inbound and outbound traffic, a proxy can also be treated differently when sending or receiving traffic from the Internet.
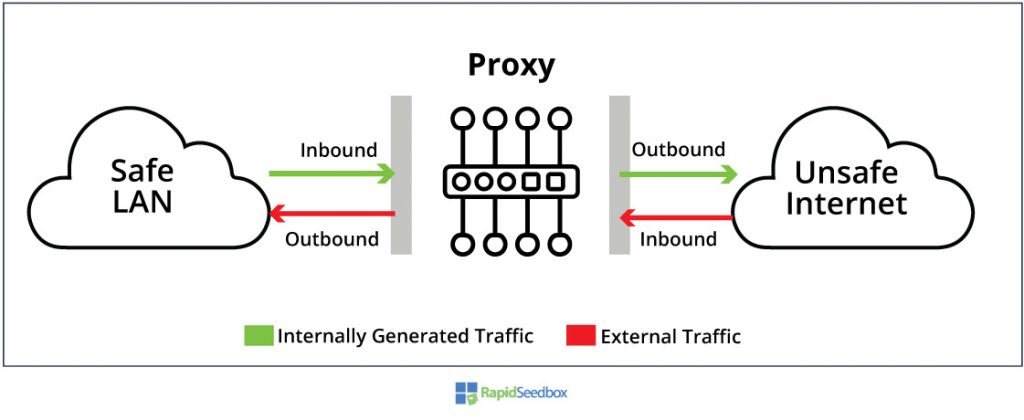
There are two popular types of proxies that face the Internet, and get different names because of their traffic flow. Although they could also be implemented internally (without Internet), the forwarding proxy and the reverse proxy are used to add protection from the Internet.
a. The Forwarding Proxy.
The forwarding proxy acts on behalf of the requesting clients. It takes inbound traffic (internal requests) and “forwards” it (or outbounds) to external resources, masking the true identities of these clients with the proxy’s identity. These proxies are used to connect and retrieve anonymously to/from resources on public networks.
b. The Reverse Proxy.
In terms of traffic direction, a reverse proxy is the opposite of a forwarding proxy. When facing the Internet, a reverse proxy takes the outbound traffic from the Internet, processes it, and forwards it to an internal network (usually a web server or service). The reverse proxy is used to protect internal resources by controlling traffic coming from the risky Internet. Reverse proxies are used to hide the identity of servers, authentication, decryption, load-balancing, caching, and compression.
3. Types of Proxy Servers Based on Anonymity Level.
Regardless of location and traffic flow— a proxy can also be classified based on the level of anonymity provided.
How to measure the degree of anonymity? — A proxy server may be able to forward all header information as exactly read from a request, a portion of it, remove header proxy’s information, or even intentionally disfigure the header to look differently.
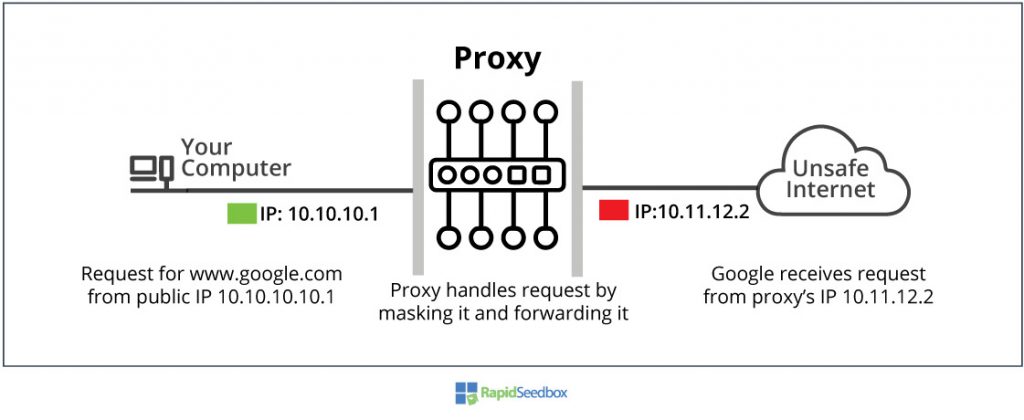
a. Transparent Proxy (Level 3).
This type of proxy does not hide the real IP address source to the target server you are connecting to. A transparent proxy does not provide anonymity. They advertise themselves as proxy servers by showing their IP in the Via header. They also pass the original IP address in the X-Forwarded-For header. Transparent proxies are often used for faster website retrieval. For example, the Caching Proxy can speed up access to frequently visited sites.
b. Anonymous Proxy (Level 2).
This type of proxy is also referred to as a Distorting Proxy and it is the most popular forwarding proxy out there. It identifies itself as a proxy but will always remain “Anonymous” by not revealing its source IP (as a transparent proxy would), instead it passes along false IP address information. Anonymous — Distorting proxy gets the name because it can show to the target server the IP address from a fake “source” geographical location. This proxy is level 2, because it still shows it is a proxy by including it in the Via field of the response header.
Anonymous rotating proxies are widely used as web browsing proxies, because they are fast, anonymous, and its rotation makes it even more difficult to detect them.
c. Elite or High-Anonymity Proxy (Level 1).
These are the top-notch anonymity proxy servers. Obviously, they do not reveal the source IP to the target server, but what makes them “elite” is that they change the fields in the response/request header that could potentially help to identify the source. First, the high-anonymity proxy servers leave no trace of being a proxy, which means they get rid of the “Via” field of the HTTP header.
Other fields within the HTTP response/request removed:
- Authorization
- From
- Proxy-Authorization
- Proxy-Connection
- Via
- X-Forwarded-For
4. Types of Proxy Servers Based on Application (and protocol).
Proxies work at the application level, which gives them an amazing level of flexibility. Because a proxy intercepts requests and responses, any network protocol can be protected, improved, or simplified with a use of a proxy.
Below is an example of an application-based proxy. The SSL Proxy is also known as SSL Server.
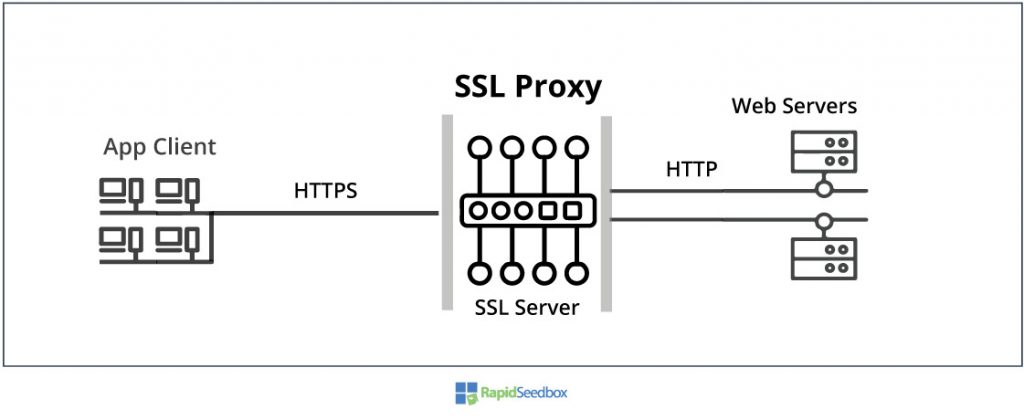
There are many types of proxy servers based on protocol possible, but the list below shows the most popular.
a. The SOCKS Proxy Server.
SOCKS (SOCKets Secure) is an Internet protocol that routes your traffic through a “third-party” server using the TCP protocol. Once your traffic goes through this server, it automatically gets a brand new IP address. This server is known as the SOCKS proxy, and your SOCKS client uses the protocol to route source packets through this server. People often confuse the SOCKS proxy with a VPN, but there is a big difference (VPNs vs Proxies)— one only changes IP, while the other encrypts traffic.
SOCKS5 is the latest version of the SOCKS protocol. It has an improved and powerful authentication system and it is fast. SOCKS5 is often used for applications that require anonymity and speed, such as torrenting and streaming.
b. The DNS Proxy.
This type of proxy could entirely take the responsibility of a DNS server— resolving a domain name to an IP address, but also the role of a DNS query forwarder, to cache and forward queries to and for other DNS servers. The DNS proxy is commonly used for improving domain lookup speed and performance.
c. The Smart DNS Proxy.
The Smart DNS is a proxy service based on DNS. It’s purpose is different from the simple DNS proxy. Smart DNS proxies are based on a SmartDNS and a proxy. When you initially try to access geo-restricted content (such as Netflix), the DNS query is sent to the SmartDNS, instead of your local DNS or Google. The Smart DNS knows that this site or service has geo restricted access so instead of resolving the domain to IP (real IP destination), it resolves the query to the proxy’s IP (which is physically located where the content is available).
Smart DNS proxies are often used as alternatives to VPN to access geo-restricted content, such as Netflix, Hulu, HBO, etc.
d. HTTP Proxy Server.
A proxy server that takes HTTP requests and response messages. It can be used for a client’s web browsing anonymity or to protect web servers. If an HTTP proxy server is used as forwarding, it simply takes all your HTTP requests and forwards them to the target HTTP server (such as a website). The HTTP Proxy server is also often used as a reverse proxy between a web client and web server to filter content. It intercepts the traffic coming from the Internet and examines it to identify suspicious activity, like spyware, harmful websites, or malformed content.
e. SMTP Proxy Server.
Simple Mail Transfer Protocol (SMTP) proxies act as mail transfer intermediaries. It is also referred to as the Anti-Spam Proxy server. The SMTP proxy is used to process and filter inbound or outbound email traffic. The inbound SMTP proxy server is useful to filter spam, viruses, limit the rate, and even to load balance SMTP traffic.
f. SSL Proxy or HTTPS Proxy Server.
The SSL proxy is a popular choice among cybersecurity experts. It can ensure SSL encryption for inbound or outbound traffic. When used as a reverse proxy, the SSL server guarantees encryption in every HTTP request or response, in order to protect the server. It provides similar security measures as a normal SSL-certified website.
The SSL proxy can also be used to scan encrypted data, filter it, and establish secure connections. The SSL proxy should be capable of decrypting and encrypting SSL traffic, so it needs to act as the SSL client and server at the same time.
g. FTP Proxy Server.
It is the intermediary for all FTP traffic. It intercepts and relays all traffic from the FTP protocol. This type of proxy is useful to control FTP connections based on different parameters, like source IP, destination IP, authentication. But it can also be used to limit the amount and rate of file transfers.
h. TOR Onion Proxy.
TOR (The Onion Router) is a worldwide network of volunteer servers that encrypt and forward traffic. By itself, TOR provides a high level of anonymity and makes Internet-tracing activities nearly impossible. Although your source IP can’t be traced back, the end-server can still identify the TOR’s exit node, AND your ISP could also recognize an entry TOR router. TOR can be used with a proxy, to make the endpoint and your ISP, unaware of TOR.
i. SEO Proxy.
Về SEO proxy is usually a type of residential rotating proxy, that helps large-scale intensive SEO campaigns remain anonymous, be fast, less prone to errors, and be reliable. When performing SEO-based web scraping, target sites or search engines can identify and block the source IP. The SEO proxy not only hides the source IP, but may also be used alongside SEO tools such as Scrapebox to analyze competition, research keywords, and even simulate traffic.
j. CGI Proxy.
A Common Gateway Interface (CGI) proxy retrieves web content from the Internet on behalf of the client. The CGI proxy is used via a web browser and looks like a normal website. To use it, you just enter the URL of the destination, and the CGI displays the results as if it was the originator of the request. The CGI proxy works via an encrypted web form embedded on another webpage using SSL. CGI proxies are used for anonymous web browsing and to unblock geo-restricted sites.
k. DHCP Proxy Agent.
This type of proxy acts as the intermediary for all DHCP requests and responses. It can be used as a DHCP server, as a DHCP relay between different subnets, and even as a DHCP client. For example, in PPP communications, the PPP server (router) may act as the DHCP client, to obtain an IP address for the user. The reasons to use a DHCP proxy agent is to protect the real DHCP server and network from attacks and even to optimize the DHCP performance of large networks.
l. SIP Proxy.
The Session Initiation Protocol (SIP) proxy, also known as the SIP server, improves the communication between two SIP endpoints. It acts as the intermediary for all SIP c alls, so it is capable of forwarding and terminating calls.
Don’t know which proxy to choose?
Experience the best with RapidSeedbox’s diverse proxy services. Whether you need anonymity, speed, or security, our proxies are designed to meet your specific requirements, backed by exceptional support.
5. Types of Proxy Based on Service.
There are providers out there (free or paid) that provide a different degree of service.
The proxy types based on a service provider may be public or private. Public proxies are risky and slow servers, but they are free. While private proxy providers guarantee privacy, speed, and reliability. A private proxy can be dedicated or shared.
Below is a proxy handling too many requests from clients.
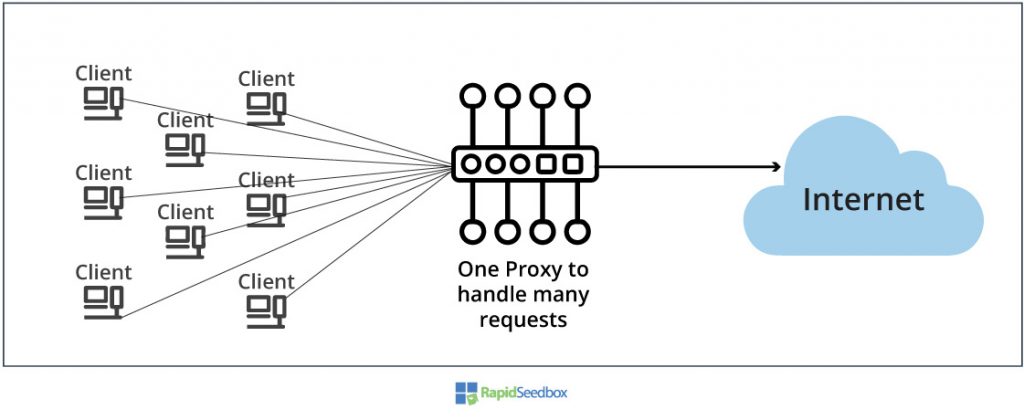
a. The Public Proxy.
These types of proxies are also known as proxy mở. They are free proxies shared by many users at the same time. They are commonly found via websites publishing updated proxy server lists. The obvious advantage of public proxies is that they are free. But the disadvantages outweigh their advantages, these proxy servers are slow, insecure, and unreliable.
b. The Private Proxy.
These types of proxies are far more reliable, fast, and secure than free public proxies. Companies providing private proxies offer other features, services, and customer support. A private proxy can be dedicated and shared.
c. The Dedicated Proxy.
Offered via hi gh-performance servers with dedicated resources like network bandwidth and processing. These types of proxies allow only one client to connect and send requests, solving the problem of “noisy neighbors” and risky blacklisting.
d. The Shared Proxy.
These are cheaper and slower than dedicated proxies, because their resources are shared with other proxy users. Shared proxies need to be powerful servers because they usually handle many requests and responses simultaneously.
6. Proxy Types Based on IP.
The types of proxy servers may also vary according to how they obtain their IP. The most popular and traditional way to obtain IPs to mask the source IP is with data-center IPs. But as proxies evolved, service providers started to get IPs from ISPs and mobile operators, then came the residential and mobile proxies.
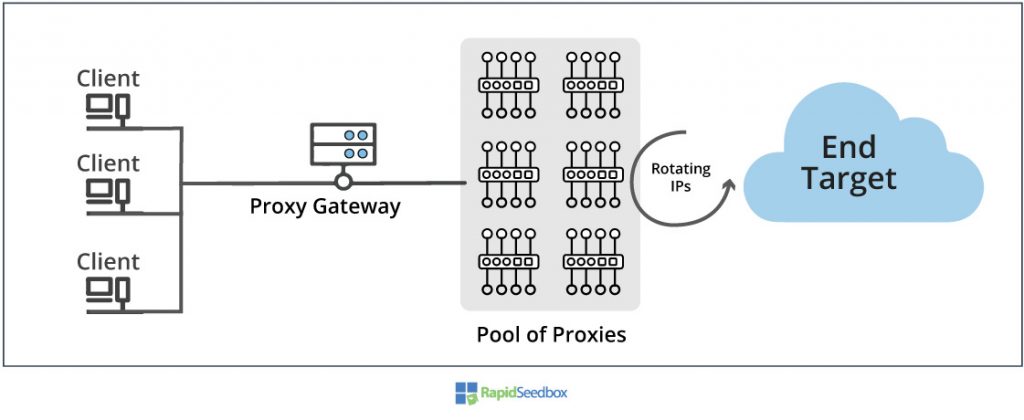
One of today’s best proxy technologies is the rotating IPv6 proxy, as shown above. This type of proxy takes a new IP from an IP pool for every new session.
a. The Data Center Proxy.
The name of these types of proxies comes from how they get the IP. These IP addresses are not affiliated with an ISP. The data center proxy uses an IP address or pool of IP addresses usually owned by LIRs (Local Internet Registries) like web hosting services.
Web servers usually block data center IPs, because their traffic doesn’t come from real humans using web browsers and real devices. Their IPs and sessions are easily flagged and identified. These types of proxies are preferred for their speed, performance, and low cost.
b. The Residential Proxy.
These are a pretty popular type of proxy server. As the name implies, these types of proxies are designed to look like real visitors requesting Internet services from their residence with their computers. The residential proxy IP addresses are associated with an ISP and other LIRs like universities, network operators, etc. These IP addresses are leased (or bought) from an ISP or LIRs that serve end-users for commercial uses (and not for residential). So regardless of how this IP was obtained, the end-point identifies it as coming from an ISP.
Some residential proxies also get their own browser information, cookies, and preferred geo-location.
Residential Proxies can be:
- Static Residential Proxy. Hide a source IP behind ONE residential IP. The advantage is that its requests look like a real visitor, so the anonymity is good. The downside is that it can’t unblock geo-restricted content from other regions.
- Rotating Residential Proxies. These types of proxies make the identity of the source behind an entire pool of unrelated IP addresses. These IP addresses are not bound to one subnet— they are a sophisticated global network of IPs. Rotating Residential Proxies switch to a brand new IP for every new connection or at a determined time interval.
Rotating proxies are frequently used for web scraping.
c. Mobile Proxy.
Also known as 3G or 4G proxy. These types of proxies hide the source IP behind a network of cellular (3G, 4G, 5G) IPs. When a desktop-user sends a request with a mobile proxy, the end-point sees as if a mobile-initiated the request. Although mobile IPs are dynamically assigned to mobile devices by the Mobile Network Operators (MNO), they can also be recognized as residential IPs. Mobile IPs are usually owned by ISPs or mobile network operators and are sometimes leased or sold to third-party proxy providers.
Mobile proxies are often used for mobile ads testing, app testing, real user experience, and more. These types of proxies are very hard to track but they are also the most expensive.
Don’t know which proxy to choose?
Experience the best with RapidSeedbox’s diverse proxy services. Whether you need anonymity, speed, or security, our proxies are designed to meet your specific requirements, backed by exceptional support.
Lời kết
Although there are many proxies to choose from, finding the right type of proxy server can be overwhelming. But once you are familiar with the different types, their pros and cons, and the alternatives— you can make wiser and more informed decisions.
We recommend, getting your network requirement and goals crystal clear beforehand. Write them on a piece of paper, so that you know exactly the type of proxy to go for.
Is it a proxy with residential IPs? or a free proxy? or perhaps a rotating proxy?
Try an optimized, anonymous, rotating IPv6 Proxy with a 24-hour money-back guarantee.
Tuyên bố miễn trừ trách nhiệm: Tài liệu này đã được phát triển nghiêm ngặt cho mục đích thông tin. Nó không cấu thành sự chứng thực cho bất kỳ hoạt động nào (bao gồm cả các hoạt động bất hợp pháp), sản phẩm hoặc dịch vụ. Bạn hoàn toàn chịu trách nhiệm tuân thủ luật hiện hành, bao gồm luật sở hữu trí tuệ, khi sử dụng dịch vụ của chúng tôi hoặc dựa vào bất kỳ thông tin nào ở đây. Chúng tôi không chấp nhận bất kỳ trách nhiệm pháp lý nào đối với thiệt hại phát sinh từ việc sử dụng các dịch vụ hoặc thông tin của chúng tôi ở đây dưới bất kỳ hình thức nào, trừ khi luật pháp yêu cầu rõ ràng.
01 bình luận