URL filtering has become a valuable tool in web control, allowing businesses to regulate which websites can be accessed within their networks. Combined with robust proxy servers, this methodology can ensure employees remain focused on work-related tasks.
By the end of this article, you’ll have a comprehensive understanding of how URL filtering works, how it can protect your network, and ensure that your organization remains compliant and secure.

Table of Contents
- What is URL Filtering?
- Pros and Cons of URL Filtering
- URL Filtering with Proxy Servers
- Steps to Implement URL Filtering with Proxy Servers
- Best Practices for Effective Web Control
- Final Thoughts
1. What is URL Filtering?
URL filtering is a cybersecurity measure organizations use to control access to specific websites within their network. By allowing or blocking access to URLs based on predefined criteria such as content type or keywords, URL filtering helps protect against malicious sites.
a. How URL Filtering Works
URL filtering functions by comparing the URLs users attempt to access against a database or set of rules defined by the organization. If a URL matches an entry on a blacklist (sites explicitly blocked), access to the site is denied.
Alternatively, a whitelist approach can be implemented, where only approved sites are accessible, and everything else is blocked. Many organizations also use category-based filtering, which allows them to block or allow entire categories of websites with a single policy.
b. Types of URL Filtering
- Blacklist Filtering: Blocks specific websites known to be harmful or inappropriate.
- Whitelist Filtering: Allows access only to sites that have been explicitly approved.
- Category-Based Filtering: Blocks or allows access to entire categories of sites (e.g., social media, adult content).
- Keyword Filtering: Filters based on specific keywords that may indicate inappropriate or harmful content.
2. Pros and Cons of URL Filtering
While URL filtering is a powerful tool for enhancing security and productivity, it has challenges. By carefully managing these challenges, organizations can leverage the advantages to create a safer, more focused online environment.
a. Advantages
URL filtering offers several benefits, making it a crucial component of an organization’s cybersecurity and productivity strategy. Below are some of the key advantages:
- Enhanced Security: Significantly reduces the risk of cyber threats by blocking access to malicious websites that could host malware, phishing schemes, or other harmful content.
- Increased Productivity: Helps ensure employees remain focused on their tasks by restricting access to non-work-related websites.
- Regulatory Compliance: Assists organizations in complying with regulations by preventing access to websites that do not meet security standards.
- Data Protection: Helps safeguard sensitive data by preventing access to sites known for phishing or data exfiltration.
- Customizable Policies: Organizations can tailor URL filtering policies to meet their needs.
b. Disadvantages
While there are several benefits, this method of web control also comes with some challenges and limitations to consider:
- Overblocking and Productivity Impact: Legitimate websites may be inadvertently blocked, potentially disrupting business activities.
- Maintenance and Updates: Cyber threats evolve rapidly, and without frequent updates to the filtering database, new malicious sites may bypass the filters.
- False Positives: May block legitimate websites incorrectly categorized as harmful or inappropriate. These can disrupt workflows.
- Performance Issues: Can introduce latency, especially in large networks with heavy traffic.
- Limited Protection Scope: Does not provide complete protection against all types of cyber threats.
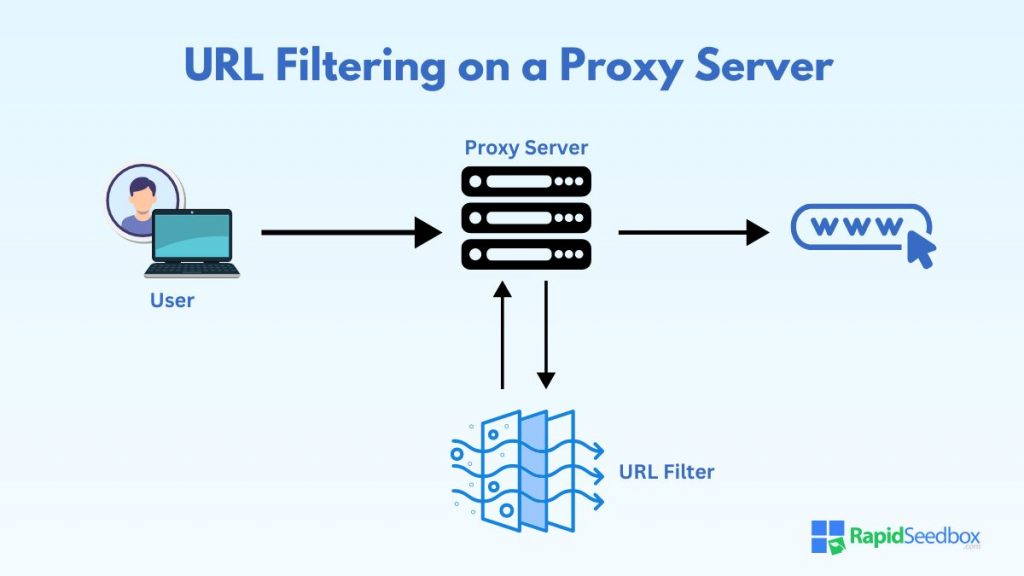
3. URL Filtering With Proxy Servers
Proxy servers aren’t new for business and have many uses. They enhance security, manage bandwidth, and enforce web usage policies. They can also filter web content, cache frequently accessed sites to improve load times and anonymize user requests to protect privacy.
When integrated with URL filtering, proxy servers become even more effective in controlling web access and safeguarding the network. Proxy servers can be robust solutions for managing web access and enhancing security.
Here’s how proxy servers work with URL filtering:
a. Centralized Control
Proxy servers provide a central point through which all web traffic passes, allowing for comprehensive monitoring and control.
Policies can be enforced at the proxy server level, ensuring that all devices on the network adhere to the same web access rules, regardless of their location or user.
b. Improved Security
By integrating URL filtering with a proxy server, organizations can prevent direct access to the internet, thereby reducing the risk of exposure to malicious websites.
The proxy server checks each URL request against the filtering criteria before allowing it through, adding an extra layer of security to the network.
c. Anonymity and Privacy
Proxy servers can anonymize user requests by masking IP addresses, making it difficult for external websites to track users’ online activities. This feature is valuable in protecting sensitive data and ensuring privacy while browsing the internet.
d. Enhanced Performance
Proxy servers often include caching mechanisms that store copies of frequently accessed web pages.
This reduces the load on external bandwidth and speeds up access to commonly visited sites. When combined with URL filtering, this can also help manage bandwidth more efficiently by restricting access to bandwidth-intensive sites that are not work-related.
e. Comprehensive Reporting and Monitoring
Proxy servers can generate detailed logs and reports on web usage, providing valuable insights into user behavior and potential security threats.
These reports can be used to refine policies, identify emerging threats, and ensure compliance with organizational web usage policies.
Ready to take control of your organization’s web traffic?
With RapidSeedbox Proxy, you can be sure of robust and flexible solutions with all the necessary features. You’re also backed by our expert customer support team, 24/7.
Start your journey to smarter web control now!
4. Steps to Implement URL Filtering with Proxy Servers
Implementing URL filtering with proxy servers requires careful planning and execution. Organizations can effectively control web access, enhance security, and maintain a productive online environment by following these steps:
Step 1: Assess Organizational Needs
Before implementing URL filtering with proxy servers, it is crucial to conduct a thorough assessment of your organization’s specific needs and requirements:
- Identify Security Concerns: Determine the primary security threats URL filtering should address, such as protection against malware, phishing, or unauthorized data access.
- Understand Productivity Goals: Identify non-work-related websites that should be blocked during work hours and any exceptions necessary for specific roles or departments.
- Compliance Requirements: Review any industry-specific regulations or internal policies the URL filtering solution must support.
- Network Infrastructure Considerations: Consider factors such as the number of users, the volume of web traffic, and the types of devices accessing the internet through the proxy.
Step 2: Choose the Right Solutions
Selecting the right tools is critical to the success of your URL filtering and proxy server implementation:
- Evaluate URL Filtering Solutions: Consider features, ease of use, and compatibility with your existing network. Key features to consider include real-time filtering, customizable policies, reporting capabilities, and the ability to integrate with proxy servers.
- Select a Suitable Proxy Server: Choose a proxy server that meets your organization’s performance, scalability, and security needs.
- Consider Vendor Support and Maintenance: Ensure the chosen solutions offer adequate support, including troubleshooting and ongoing maintenance.
Step 3: Define Policies

Once the tools are selected, the next step is to define and configure URL filtering policies:
- Set Filtering Criteria: This may include blacklisting specific URLs, whitelisting essential sites, and implementing category-based filtering.
- Create Role-Based Access Controls: Tailor policies based on user roles or departments within the organization.
- Establish Time-Based Policies: Consider implementing time-based filtering policies that restrict access to certain websites during work hours but allow more freedom during breaks.
- Document Policies: This helps set expectations and reduces the likelihood of policy violations.
Step 4: Configure Proxy Servers
With policies in place, it’s time to configure the proxy servers to enforce these policies effectively:
- Install and Set Up the Proxy Server: Deploy the chosen proxy server solution. You can also work with remote proxies for off-premise network solutions.
- Integrate URL Filtering: Integrate the proxy server with the URL filtering solution and configure it to enforce policies.
- Configure Caching and Performance Settings: Optimize the proxy server’s caching settings to improve performance, especially for frequently accessed sites.
- Set Up Monitoring and Logging: This will provide valuable insights into web usage patterns and help identify potential security threats or policy violations.
5. Best Practices for Effective Web Control
Implementing URL filtering and proxy servers is just the beginning of establishing effective web control within an organization. To maximize the benefits of these tools and ensure they continue to meet the organization’s needs, it’s essential to follow best practices.
These practices help maintain a secure, efficient, and compliant online environment, balancing security with usability.
a. Regularly Update URL Filtering Databases
One of the most critical aspects of maintaining effective web control is ensuring that the URL filtering database is regularly updated:
- Stay Ahead of Emerging Threats: Cyber threats constantly evolve, with new malicious websites appearing daily.
- Ensure Accurate Categorization: Websites frequently change their content or purpose, leading to inaccurate filtering with outdated databases.
- Automate Updates: This reduces the burden on IT staff and ensures that your filtering system always operates with the latest information.
b. Monitor and Optimize Proxy Server Performance
Proxy servers play a crucial role in web control but can also become bottlenecks if not correctly managed. Monitoring and optimizing performance is essential:
- Monitor Traffic and Latency: High traffic volumes can slow down the network, so it’s essential to ensure that the proxy server can handle the load without degrading user experience.
- Optimize Caching: This can significantly reduce load times for users and decrease bandwidth usage, leading to a more responsive network.
- Balance Load Across Multiple Servers: To distribute traffic evenly in more extensive networks, consider using multiple proxy servers and implementing load balancing.
c. Implement Layered Security
While URL filtering and proxy servers are powerful tools, they should be part of a broader, layered security strategy:
- Combine with Firewalls and Intrusion Detection Systems: Firewalls can block unauthorized access at the network perimeter, while IDS can detect and respond to suspicious activities that might bypass other defenses.
- Utilize Endpoint Protection: This helps protect against threats from sources other than the web, such as USB drives or phishing emails.
- Regularly Review Security Policies: Ensure these policies are comprehensive, covering not just web access but all network and data security aspects.
6. Final Thoughts
Effective web control is essential for any organization that wants to protect its network, ensure compliance with regulations, and maintain a productive work environment. URL filtering, when combined with proxy servers, provides a powerful and flexible solution to achieve these goals.
However, successfully implementing this tool requires careful planning and ongoing management. Organizations must assess their needs, choose the right tools, and define comprehensive policies aligning with their security and productivity objectives.
Looking to implement web access effectively?
RapidSeedbox Proxy solutions are designed to enhance security without compromising on speed, ensuring your network remains protected and efficient.
0Comments