Yes, torrenting can get you hacked because it exposes you to serious security risks. When you use a torrent client, you connect to a network of strangers. This allows hackers to sneak malware or viruses onto your device.

Table of Contents
- How Torrenting Can Lead to Hacking
- Common Ways Torrenting Exposes You to Hackers
- How to Stay Safe While Torrenting
- Examples of Torrenting-Related Hacks
- What to Do If You’ve Been Hacked After Torrenting
- Frequently Asked Questions
- Final Thoughts
1. How Torrenting Can Lead to Hacking
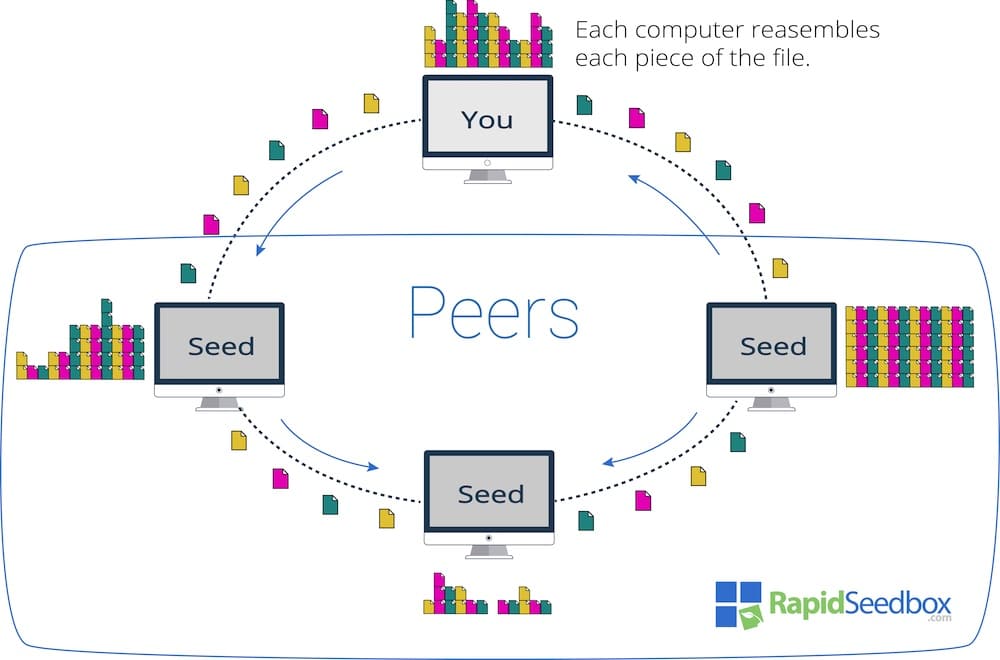
Knowing how torrenting works is essential to learning how your system may get compromised. Instead of downloading a file from one source, you download bits from many different people and upload parts of the file for others to download.
The very nature of torrenting opens up several potential vulnerabilities. Hackers can easily infiltrate these networks by uploading files that appear legitimate but are laced with harmful software.
2. Common Ways Torrenting Exposes You to Hackers
Hackers use various methods to exploit torrent downloaders. These include infected files, exploiting vulnerabilities, or stealing data in transit.
Here are some of the most common tactics they use:
a. Malware-Infested Files
Hackers can disguise malware as popular content, such as a new movie release or a software update. These malicious files might look normal, but once opened, they can install harmful programs that damage your system or steal your data.
b. Man-in-the-Middle Attacks
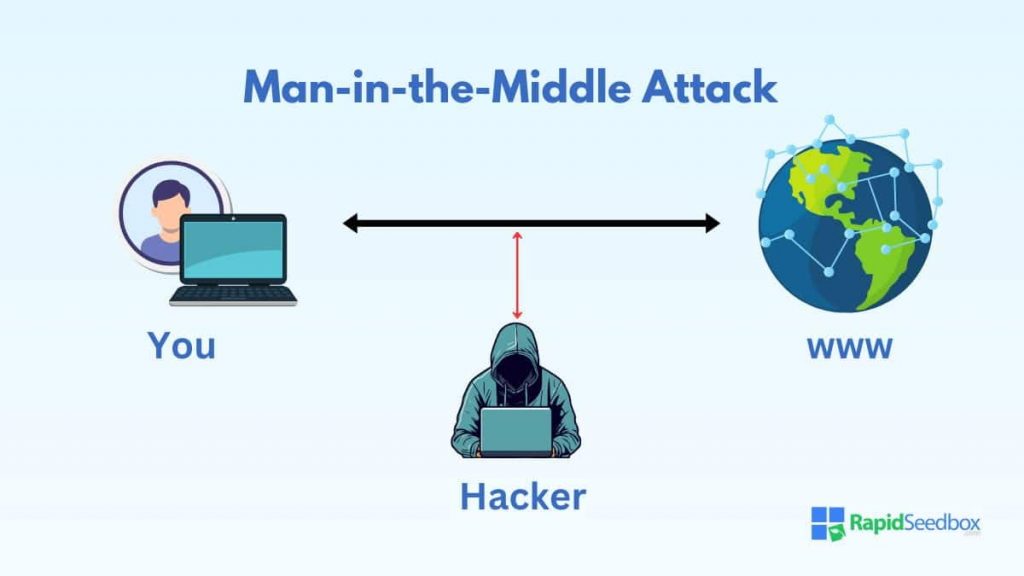
In this scenario, a hacker intercepts the data being exchanged between you and other peers on the network, allowing them to inject malware into the file you’re downloading or steal sensitive information, like your IP address or browsing history.
c. Seeding with Malicious Code
In torrenting, “seeders” are users who have a complete file and are sharing it with others. Hackers can act as seeders by distributing files infected with malware or viruses. When you download from a malicious seeder, you may download harmful code.
d. Exploitation of System Vulnerabilities
Some malware targets vulnerabilities in your operating system or software. You risk downloading files containing scripts designed to exploit these weaknesses when you torrent from untrusted sources.
For example, a hacker might embed code in a torrent that exploits outdated software, allowing them to control your device or install spyware without your knowledge.
3. How to Stay Safe While Torrenting
Torrenting can be risky, but there are ways to protect yourself and lower your chances of downloading malware or being tracked.
Here’s how to stay safe:
a. Use a Seedbox
A seedbox is a private server used for safely downloading and uploading torrents. Instead of downloading torrents directly to your computer, the seedbox downloads them. Once done, you can move the files to your computer via a secure connection, like FTP.
b. Use a VPN
A Virtual Private Network (VPN) is one of the best ways to stay safe while torrenting. It hides your IP address and encrypts your internet traffic, making it harder for anyone to see what you’re doing online.
c. Avoid Downloading Executable Files
Executable files (.exe, .bat, etc.) are more likely to contain viruses or malware, especially from torrents. If possible, stick to downloading media files like videos or music, which are less likely to carry malware.
d. Check Comments and Reviews
Before downloading a file, always take a moment to read the comments or reviews left by other users. If the torrent contains malware, someone will likely warn others in the comments section. It’s a quick and easy way to avoid potentially harmful files.
Looking for a safer way to torrent?
RapidSeedbox is the ideal solution for safe and private downloads. A seedbox keeps your torrenting activity off your device, reducing the risk of malware and hacking.
Torrent safely now with RapidSeedbox!
4. Examples of Torrenting-Related Hacks
If you aren’t convinced that hacking incidents can happen while torrenting, there are many examples of it happening in the past.
Here are some notable incidents:
a. The Game of Thrones Malware Attack
When the popular show Game of Thrones was released, many fans downloaded fake torrents that claimed to have new episodes. These files contained malware that infected over 20,934 users.
b. Pirate Bay Malware
The popular torrent site The Pirate Bay has been a hotspot for fake torrents. Even worse, it has many clones, exponentially increasing the risk. These sites have served millions of fake torrents and malicious ads to users.
c. Cracksnow Malware Distribution
One famous torrent uploader, Cracksnow, distributed millions of infected torrents via popular sites, including 1337x and The Pirate Bay. The torrents included ransomware that locked devices and demanded cryptocurrency for an unlock key.
5. What to Do If You’ve Been Hacked After Torrenting
If you think you’ve been hacked after downloading a torrent, you must act quickly to minimize the damage. Here’s how you can protect yourself and your device:
Step 1. Disconnect from the Internet
By disconnecting from the internet, you stop hackers from continuing to access your computer. It also prevents any ongoing data transfer or control the hacker might have over your system.
How to Do It:
- For a WiFi Connection: Click on your WiFi icon (usually in the bottom-right corner of your screen) and turn off your WiFi connection. You can also physically unplug your router if needed.
- For a Wired Connection: Unplug the Ethernet cable from your computer to stop the internet connection immediately.
Step 2. Scan with Antivirus Software
A complete system scan will check every file on your computer for malware or suspicious activity. The antivirus software will remove or quarantine the malware, preventing it from causing further damage.
How to Do It:
- Windows: Open your antivirus software and look for an option that says “Full Scan” or “Complete System Scan.” This option thoroughly checks all your files and folders.
- Mac: If you have antivirus software installed, follow the same steps.
Note: Use a trusted antivirus brand like Norton, ESET, or Bitdefender. Malwarebytes is also a good choice for malware detection and cleaning.
Step 3. Look for Signs of a Hack
Recognizing the symptoms of a hack allows you to act faster. If something feels off—like slow performance or programs you don’t recognize—it’s a sign your computer may have been compromised.
How to Recognize Possible Hack Symptoms:
- Unexplained Pop-Ups or Programs: To check for programs running in the background, press Ctrl + Shift + Esc (Windows) or open Activity Monitor (Mac) to see if any unfamiliar programs are running.
- Slow Performance: If your computer is slower than usual after torrenting, open Task Manager (Windows) or Activity Monitor (Mac) to see if unknown processes use memory or CPU power.
- Suspicious Internet Activity: Check your internet usage by opening the Task Manager (Windows) or Activity Monitor (Mac). Go to the “Network” tab to see if there is high data usage even when you’re not doing anything online.
Step 4. Change Your Passwords
Changing your passwords limits the damage hackers can do if they gain access to your accounts. Doing it from a secure device ensures that the hacker can’t interfere while you secure your accounts.
How to Do It:
- From Another Device: If you believe your computer is hacked, use a secure device (like your phone or another computer) to change passwords for important accounts like your email, social media, and bank accounts.
- Use Strong Passwords: When changing your passwords, make sure they are strong—include a mix of letters (both uppercase and lowercase), numbers, and symbols.
- Enable 2FA: Enable Two-Factor Authentication for your accounts. This adds an extra layer of security by requiring a separate verification code.
Step 5. Seek Professional Help if Necessary
Professional technicians have the experience and tools to deal with complex malware infections or serious hacks. They can help you regain control of your system and ensure no traces of the hack remain.
How to Do It:
- Contact a Tech Support Service: Many companies offer remote help. They can guide you through steps or even remove malware remotely.
- Visit a Local Repair Shop: They have specialized tools and knowledge to detect and remove malware, repair corrupted files, and secure your system.
- Backup Your Data: Before seeking professional help, back up any critical files to an external hard drive.
6. Frequently Asked Questions
Yes, but it requires caution. To torrent safely, you should use a VPN to protect your privacy, only download files from trusted sources, and run a reliable antivirus program to scan files before opening them.
The chances of getting malware from torrenting are relatively high, especially if you download files from unverified or less popular torrent sites. Hackers often target popular torrent sites, uploading files with hidden malware.
No, a VPN doesn’t provide complete protection. While a VPN hides your IP address and encrypts your internet connection, making it harder for hackers to track or steal your data, it doesn’t prevent you from downloading infected files.
Yes, it’s possible. Some torrent sites are poorly secured and can be infected with malicious ads or links. Even if you don’t download anything, visiting the site can expose your device to malware through malicious pop-ups, ads, or scripts embedded in the website.
Yes, seeding can increase your risk. When you seed, you share parts of a file with others on the torrent network. This keeps your connection active and exposes your IP address for longer, which can be risky.
7. Final Thoughts
Torrenting can be convenient, but it comes with serious risks, including getting hacked, downloading malware, or facing legal trouble. Hackers often use torrent files to spread harmful software, and your privacy can be at risk if you’re not careful.
The good news is that using a seedbox or a VPN can make torrenting much safer. However, no method is foolproof, and there’s always some risk involved.
Want to torrent faster and safer?
RapidSeedbox offers a fast, secure, and private way to download files without compromising security. By using a seedbox, you can safely torrent while keeping your IP hidden and your connection encrypted.
0Comments