The term proxy sites is broad since it covers several items under one umbrella. However, focusing on the word proxy, the general direction of these sites is to provide access convenience. The burning question, though, is, are proxy sites safe?
One primary reason people distrust proxy sites is that almost anyone can set one up. Therefore, security and privacy have become unknown factors, which is concerning in this age of increasing cyber threats.
This article takes a deeper dive into proxy sites and assesses the level of concern they bring to the public.

Disclaimer: This material has been developed strictly for informational purposes. It does not constitute endorsement of any activities (including illegal activities), products or services. You are solely responsible for complying with the applicable laws, including intellectual property laws, when using our services or relying on any information herein. We do not accept any liability for damage arising from the use of our services or information contained herein in any manner whatsoever, except where explicitly required by law.
Table of Contents
- Are Proxy Sites Safe?
- Why Proxy Sites May be Dangerous
- How to Use Proxy Sites Safely
- Alternatives to Proxy Sites
- Final Thoughts
1. Are Proxy Sites Safe?
Proxy sites can be safe, depending on your chosen proxy type and service provider. However, while some reputable proxy service providers exist, most are high-risk. That’s especially so for free or public proxies, which may log data or inject malware.
a. What Are Proxy Sites?
Proxy sites are online services that act as intermediaries between a user’s device and the internet. Many use proxy sites to bypass geographic restrictions, access blocked websites, or enhance online privacy.
There are various proxy site types, including public, private, and web-based proxies, each offering different levels of security, speed, and reliability.
b. How Proxy Sites Work
Proxy sites sit between your device and the general Internet. When you enter a website address into a proxy site, your request is sent to the proxy server first. The proxy server then forwards your request to the destination website, retrieves the content, and sends it back to you.
Throughout this process, the destination website only sees the proxy server’s IP address, not yours, which helps mask your identity.
c. Common Uses of Proxy Sites
Proxy sites are used for various purposes, each catering to different needs:
- Bypassing Geographic Restrictions: Many users use proxy sites to access restricted content in their country or region. This is common for streaming services, news websites, and social media platforms that limit their content geographically.
- Maintaining Anonymity: Proxy sites help users browse the web anonymously by masking their IP addresses. This is useful for individuals concerned about online privacy, as it prevents websites and online services from tracking their location and browsing habits.
- Accessing Blocked Websites: In environments where internet access is restricted, such as in schools, workplaces, or certain countries, proxy sites are commonly used to bypass these restrictions and access blocked websites.
- Content Filtering and Monitoring: Organizations often use proxy sites to control and monitor their employees’ or users’ web traffic. Proxies can filter content, block access to certain types of websites, and monitor internet usage to ensure compliance with company policies.
d. Examples of Proxy Sites
Numerous proxy sites are available online, each offering different features and service levels. Here are a few examples:
- Hidester: A free proxy service that allows users to browse the web anonymously. It includes options to choose between different proxy servers and performs data encryption.
- KProxy: A widely used proxy service offering a web-based proxy and a browser extension. KProxy is known for its user-friendly interface and ability to bypass most restrictions.
- Proxysite.com: A free, web-based proxy that allows users to access blocked websites easily. It offers a selection of proxy servers in different locations.
Want a reliable and secure proxy?
Unlike free proxies that often log your data and compromise security, RapidSeedbox ensures your information stays private with robust encryption and a strict no-logs policy.
2. Why Proxy Sites May be Dangerous
While proxy sites can offer benefits like anonymity and access to restricted content, they also have several significant risks. Understanding the risks you may take if you use these services is essential.
Note: While all proxy services carry some risk, free proxies are notoriously dangerous and often threaten privacy and security.
a. Data Privacy Concerns
One of the most significant risks associated with using proxy sites is the potential for data logging. Some proxy services, especially free ones, may track your browsing activity, collect personal data, or log the websites you visit.
This information is often sold to third parties, including advertisers or malicious entities. The anonymity you seek when using a proxy can be compromised if the service provider logs and misuses that data.
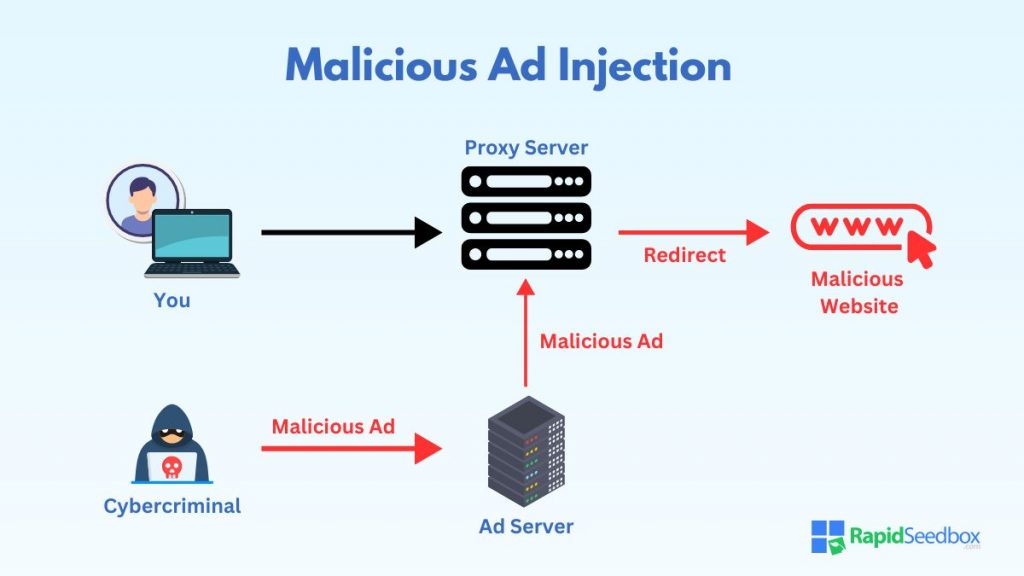
b. Malware and Security Threats
Free or poorly regulated proxy sites are often associated with security risks, including malware distribution. Some proxies inject ads or malicious code into the data they relay to your device. This may cause your device to be infected with malware, spyware, or other harmful software.
In some cases, these malicious proxies are expressly set up to harvest sensitive information, such as login credentials or financial details. The lack of security protocols in many proxies increases the risk of encountering such threats.
c. Unreliable Performance
Using a proxy site can significantly impact your internet speed and connection reliability. Many free proxy services are overcrowded with users, leading to slow browsing speeds, frequent disconnections, and poor performance.
Additionally, because free proxies are often not well-maintained, they can suffer from downtime, making them unreliable for consistent use. These performance issues can be a significant drawback if you rely on proxies to access critical information or services.
d. Lack of Encryption
Another significant risk is the lack of encryption in many proxy services. If the proxy does not use HTTPS (a secure version of HTTP), your data is transmitted in plain text.
Anyone intercepting your connection—a hacker or the proxy service itself—can easily read your data, including passwords, personal messages, and other sensitive information. Without encryption, using a proxy can increase your vulnerability to cyberattacks rather than protect you from them.
e. Potential Legal Implications
While proxy sites can help you bypass geographic restrictions or access blocked content, doing so may violate the terms of service of certain websites or even local laws. For example, accessing restricted content in your country could have legal consequences.
Additionally, some countries have strict laws against using proxies or VPNs to circumvent censorship; violating these laws could lead to fines or other penalties.
3. How to Use Proxy Sites Safely
While proxy sites come with inherent risks, there are steps you can take to use them more safely. You can mitigate some risks by following best practices and being mindful of the potential dangers.
a. Choose a Reputable Proxy Provider
The first and most crucial step in using a proxy site safely is selecting a reputable provider. Not all proxies are created equal; some may be set up expressly to exploit users. When choosing a proxy service, consider the following:
- Research the Provider: Look for reviews and feedback from other users. Reliable proxy services will have a robust online presence and positive reviews from trusted sources.
- Check the Privacy Policy: Ensure the proxy provider has a clear and transparent privacy policy. This document should outline how your data is collected and handled.
- Avoid Free Proxies: While free proxies might be tempting, they often come with hidden costs, such as data logging, ads, or security vulnerabilities.
b. Use Proxies with HTTPS Encryption
Always ensure that your proxy service supports HTTPS, which encrypts the data between your device and the proxy server. This is crucial for protecting your information from being intercepted by third parties.
When using a proxy, look for the “https://” prefix in the URL bar, indicating that the connection is encrypted. If a proxy site only offers HTTP (without the “S”), it’s best to avoid it, especially when handling sensitive information.
c. Combine Proxies with Other Security Tools
For enhanced security, consider combining the use of a proxy with other privacy tools:
- Virtual Private Network: A VPN encrypts all your internet traffic and routes it through a secure server, offering higher security than a standard proxy. Combining a VPN and proxy can provide more protection but may lower your Internet speed.
- Secure Browsers: Browsers like Tor are designed to protect user anonymity by routing traffic through multiple servers and encrypting it at each stage.
- Internet Security Apps: You should always have an Internet security app active. These may help catch any malware or trackers that malicious proxies try to inject.
d. Avoid Entering Sensitive Information
When using a proxy, it’s best to avoid entering sensitive information such as passwords, credit card details, or personal identification numbers (PINs). Since proxies can potentially log data or lack encryption, any information you transmit could be at risk.
If you need to perform tasks requiring sensitive data, such as online banking or shopping, using a VPN or a direct, secure connection is safer than relying on a proxy.
e. Regularly Clear Cookies and Cache
Proxy sites can store cookies and cache data from the websites you visit. Regularly clear your browser’s cookies and cache to prevent tracking or data leaks. This can help maintain your privacy by ensuring that old data is inaccessible.
4. Alternatives to Proxy Sites
While proxy sites can be helpful for specific tasks, they are seldom the most well-regarded in maintaining privacy and security. If these are your objectives, consider the following alternatives instead:
a. Virtual Private Networks
VPNs are one of the most effective alternatives to proxy sites. A VPN creates a secure, encrypted tunnel between your device and the internet, routing your traffic through a remote server.
This process masks your IP address and encrypts all data transmitted between your device and the VPN server, offering higher security than most proxy sites.
Benefits of using a VPN include:
- Strong Encryption
- Enhanced Privacy
- Bypassing Geo-Restrictions
- Many Server Locations
b. Tor Network
The Onion Router, or Tor Network, is another powerful alternative to proxy sites, especially for those who prioritize anonymity. Tor is a free, open-source network that anonymizes your internet activity by routing it through a series of volunteer-operated servers, also known as nodes.
Each time your data passes through a node, it is encrypted and re-encrypted, making it extremely difficult for anyone to trace your activity back to you.
Benefits of Using Tor:
- High Anonymity
- May Bypass Censorship
- No Centralized Control
Limitations of Tor: Tor offers strong anonymity but can be slower than other alternatives due to the multiple encryption layers and the number of nodes your data must pass through. Additionally, Tor is often associated with illegal activities on the dark web, which can sometimes lead to scrutiny by authorities.
c. Smart DNS Services
Smart DNS focuses on bypassing geo-restrictions rather than providing anonymity. A Smart DNS service reroutes only the traffic related to your geographic location, such as the DNS queries used to determine your location.
Unlike a VPN, Smart DNS does not encrypt your traffic or hide your IP address, so it is not intended for privacy protection. However, this lack of encryption means there is minimal impact on your Internet speeds.
Benefits of using Smart DNS:
- High Speed
- Bypassing Geo-Restrictions
- Easy Setup
Limitations of Smart DNS: Because Smart DNS does not encrypt your data or hide your IP address, it does not offer the same level of security or privacy as VPNs or Tor. It is primarily suited for users who must bypass geo-restrictions without compromising speed.
5. Final Thoughts
Proxy sites can help achieve anonymity and bypass restrictions online, but many come with significant risks that cannot be ignored. While some reputable proxy services offer a degree of security, many, mainly free or poorly managed, pose a considerable threat.
However, remember that some premium proxy service providers do an excellent job. These are often highly reputable and have robust, secure servers that you can use for almost any purpose, from anonymization to data collection activities.
Is your current proxy service putting your data at risk?
Switch to RapidSeedbox Proxy for a secure and trustworthy solution. RapidSeedbox prioritizes your privacy and protects you from the risks associated with lesser proxy services.

0Comments