One tool often mentioned in discussions about online privacy is the proxy server. Proxy servers help hide your IP address, thereby providing some level of digital anonymity. But how far does a proxy hide your identity, and are they reliable?
While these questions may seem like we’re splitting hairs, they’re a valid concern. Not knowing the specifics could land you as much trouble as surfing the web without protection. Remember that everyone is after your data today—legitimate companies and cybercriminals alike.
Table of Contents
- Does a Proxy Hide Your Identity?
- Limitations of Proxies in Hiding Identity
- Comparing Proxies With Other Privacy Tools
- How to Enhance Your Anonymity When Using Proxies
- Frequently Asked Questions
- Final Thoughts
1. Does a Proxy Hide Your Identity?
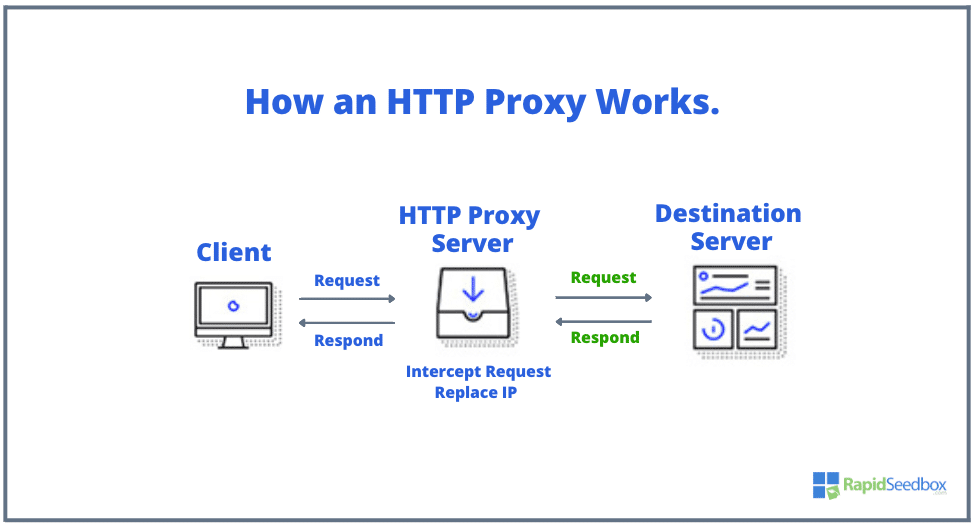
A proxy primarily hides your IP address, providing some level of anonymity. However, it does not completely hide your identity. Other identifying information, such as browser fingerprinting and cookies, can still reveal your identity.
Proxy services work by rerouting your internet traffic through their servers. During this process, your IP address is replaced by the server’s. When you visit a website via a proxy connection, the website sees the IP address of the proxy server instead of your actual IP address.
While this sounds plausible to hide your identity, it’s far from perfect.
2. Limitations of Proxies in Hiding Identity
Now that we know proxies can’t entirely protect your identity, let’s learn more about the extent to which they work. Understanding these limitations is essential to making your choice of anonymization tools.
a. Proxies and Personal Information
Browser Fingerprinting
One significant limitation of proxies is their inability to prevent browser fingerprinting. Websites can gather detailed information about your browser settings, including:
- Browser type and version
- Operating system
- Screen resolution
- Installed plugins
- Timezone and language settings
This combination of information creates a unique fingerprint that websites can use to track your online activity across sessions, even if a proxy hides your IP address.
Cookies and Tracking Technologies
Proxies do not block cookies or other tracking technologies used by websites to monitor your online behavior. These cookies can store information about browsing habits, preferences, and even login details, linking your activities across different websites and sessions.
As a result, even if your IP address is masked, cookies can still compromise your privacy by revealing your identity or connecting you to various online activities.
b. Proxies and Data Encryption
Most proxies do not encrypt the data transmitted between your device and the proxy server. This lack of encryption means third parties, such as ISPs, hackers, or government agencies, can intercept and monitor your internet traffic.
Note: Unencrypted data can expose sensitive information like login credentials, financial details, and personal messages.
While HTTPS proxies provide some level of encryption, they only encrypt the data between your device and the proxy server, not the entire path to the final destination. This partial encryption is less robust than the end-to-end encryption offered by Virtual Private Networks (VPNs).
c. Proxies and Trustworthiness
The level of anonymity and security provided by a proxy, in part, depends on the trustworthiness of the proxy provider. Key concerns include:
- Logging Practices: Some proxy providers, especially free ones, may log your internet activity and sell the data to third parties.
- Malware Risks: Less reputable proxy services might inject malware or ads into your browsing sessions, posing additional security risks.
- Reliability: Free proxies often suffer from slow speeds, frequent downtime, and limited bandwidth, which can expose your activities if the proxy fails.
d. Proxy Detection and Blocking
Many websites and online services have become adept at detecting and blocking proxy traffic. Techniques used to identify proxies include:
- IP Blacklisting: Websites maintain lists of known proxy IP addresses and block any traffic originating from these addresses.
- Traffic Analysis: Advanced algorithms analyze traffic patterns to identify and block proxy use.
Want a reputable and reliable proxy?
With RapidSeedbox Proxy, you can mask your IP address and keep your online activities private. Our proxies ensure that your real IP is never exposed, allowing you to surf the web without fear of being tracked.
Take control of your online privacy now!
3. Comparing Proxies With Other Privacy Tools
| Feature | Proxy | VPN | Tor |
| IP Masking | Yes | Yes | Yes |
| Encryption | Sometimes | Yes | Partial |
| Anonymity | Low | Medium | High |
| Speed | Fast | Fast | Slow |
Given the limitations of proxies, we are thankful that there are alternatives that can also hide your identity. Each has pros and cons, so choosing is a matter of your use case.
a. Proxies vs. VPNs
VPNs are one of the most popular alternatives to proxies for hiding identity. While they share some similarities, such as IP address masking, they differ significantly in data encryption, speed, and overall security.
Key Differences
- IP Address Masking: Proxies and VPNs mask your IP address, but VPNs route all your internet traffic through an encrypted tunnel, while proxies typically only route specific types of traffic (e.g., HTTP or SOCKS).
- Data Encryption: VPNs encrypt all data transmitted between your device and the VPN server, providing higher security against data interception. Most proxies do not encrypt your data.
- Speed and Performance: Proxies may sometimes be faster than VPNs because they generally do not encrypt data. However, a powerful device and a good VPN provider can reduce the performance discrepancy.
Which Should You Choose?
- Proxies: Best for casual browsing, accessing geo-restricted content, and bypassing network restrictions where high-level security is not a critical concern.
- VPNs: Ideal for secure online activities, such as banking, confidential communications, and protecting personal data on public WiFi networks.
4.2 Proxies vs. Tor
For those seeking the highest level of online anonymity, Tor and proxies offer distinct approaches. Tor’s multi-layered routing provides superior anonymity to proxies but at the expense of speed.
Key Differences
- Anonymity: Tor provides better anonymity than proxies. It routes your traffic through multiple volunteer-operated nodes (relays). Each relay only knows the previous and next relay, making it extremely difficult to trace the traffic back to the source.
- Speed: Tor can be significantly slower than proxies due to its multi-layered routing and the limited bandwidth of volunteer nodes.
- Compatibility: Tor requires specific software (Tor Browser) and might not be compatible with all internet activities, especially those requiring high bandwidth.
Which Should You Choose?
- Proxies: Suitable for quick and straightforward tasks like bypassing geo-restrictions and accessing blocked content.
- Tor: Best for activities requiring high anonymity and privacy, such as whistleblowing, sensitive communications, and accessing the dark web.
4. How to Enhance Your Anonymity When Using Proxies
Proxies and other privacy tools can be combined with safe browsing habits to increase online anonymity. Combining the right tools with these habits can result in a safer digital experience. Consider implementing these changes:
- Manage Cookies Regularly: Clear cookies and browsing data to prevent websites from tracking your activities. Some browsers allow you to automate this process to ensure data is deleted after each session.
- Private Browsing Mode: Use private or incognito mode in your browser to prevent it from storing cookies, history, and other browsing data during your session.
- Privacy Browsers: Switch to browsers prioritizing user privacy, such as Mozilla Firefox or Brave. These browsers come with features to block trackers and enhance security.
- Privacy Extensions: Install browser extensions like uBlock Origin, Privacy Badger, and HTTPS Everywhere to block ads and trackers.
- Avoid Sharing Personal Information: Be cautious about sharing personal information such as your full name, address, phone number, and email address online.
- Monitor Permissions: Regularly review the permissions granted to apps and websites. Limit access to your data and revoke permissions that are not necessary.
- Keep Software Updated: Regularly update your browser, operating system, and any privacy tools you use.
- Use Security Software: Install and maintain reputable security software on your devices to protect against malware, spyware, and other threats.
5. Frequently Asked Questions
A proxy hides your IP address by routing your internet traffic through its own server. The target website sees the request coming from the proxy server’s IP address instead of your own, masking your real IP address.
Some websites can detect and block proxy usage through advanced detection techniques. However, elite proxies, which do not reveal the use of a proxy, are more challenging to detect.
Free proxy services can pose risks such as data logging, malware, and a lack of encryption. Using reputable paid proxy services offering better security and privacy policies is safer.
No. Netflix requires users to log in with their account to use the service so it will always know their identity. However, some proxies may bypass Netflix’s geo-restrictions, allowing users to access different content libraries.
Setting up a proxy varies by device and browser. Generally, it involves entering the proxy server address and port in the network settings of your operating system or browser. Detailed instructions can usually be found on the proxy provider’s website.
6. Final Thoughts
While proxies offer a helpful layer of anonymity by masking your IP address, they are not a comprehensive solution for hiding your identity online. However, they offer advantages, such as helping you access geo-restricted content and bypassing network restrictions.
For more robust online privacy, consider using proxies with other privacy tools such as VPNs, which offer full data encryption, or the Tor network, which provides high levels of anonymity. The most vital aspect is to combine privacy tools with safe browsing habits.
Want bulletproof identity protection?
With RapidSeedbox VPN, your data remains private and secure, no matter where you are. Experience the highest level of online privacy with top-notch encryption and IP masking by subscribing to RapidSeedbox VPN today.
0Comments