One of the simplest yet effective methods of safeguarding systems is through IP whitelisting. It is particularly beneficial for businesses that rely on remote access or have distributed teams but want to maintain strict security protocols.
This guide is designed for beginners, whether you’re an IT administrator, business owner, or just curious about online security. We will cover the fundamentals, use cases, implementation steps, and how IP whitelisting integrates with other security measures like proxy servers.

Table of Contents
- What is IP Whitelisting?
- How Does IP Whitelisting Work?
- Advantages of IP Whitelisting
- How to Implement IP Whitelisting
- Best Practices for Managing IP Whitelists
- Final Thoughts
1. What is IP Whitelisting?
IP whitelisting is a security practice that involves creating a list of trusted IP addresses granted access to a specific server, application, or network. By using IP whitelisting, only pre-approved IP addresses can interact with your system.
By restricting access to a select group of devices based on their IP addresses, you can limit exposure to potential attacks and unauthorized access. The method effectively controls access to critical business systems, cloud infrastructure, and online services.
Common Use Cases:
- Website Administration: Only specific IPs can access backend dashboards or administrative control panels.
- Corporate Networks: Restricting access to internal systems like databases or file servers, ensuring that only trusted devices can connect.
- API Protection: Ensures that only approved IP addresses can send requests.
- Cloud Services: Limiting access to cloud environments such as AWS or Azure to specific IP addresses to prevent unauthorized access.
2. How Does IP Whitelisting Work?
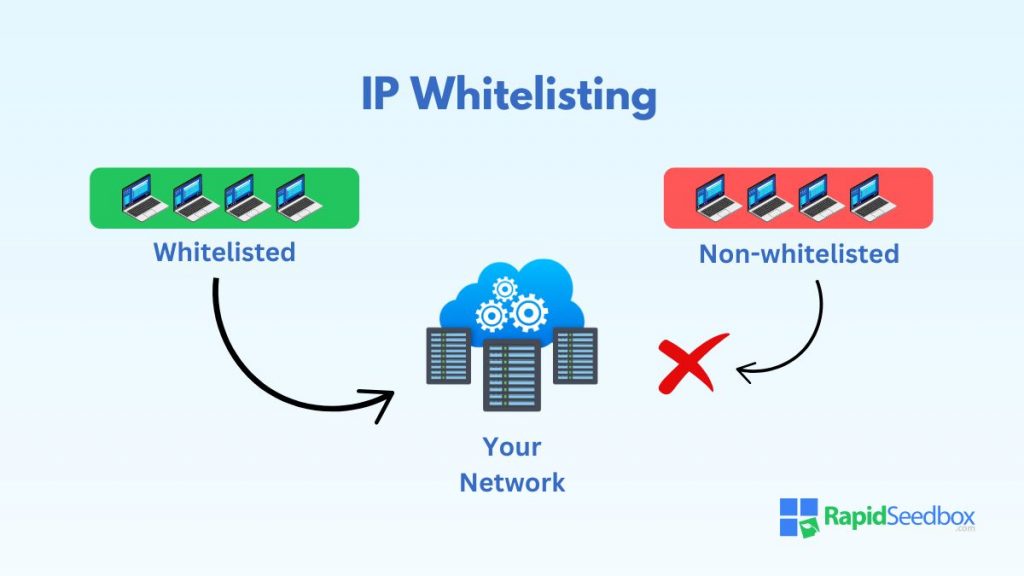
IP whitelisting only allows access from pre-approved IP addresses. The process revolves around configuring proxy servers, firewalls, routers, or application settings to create and enforce a list of trusted IP addresses.
Here’s how the process typically works:
Step 1. Identifying Trusted IPs: Collect the specific IP addresses of those users or devices that need access.
Step 2. Configuring the Whitelist: This can be done through network hardware or directly within applications.
Step 3. Enforcing Access Control: Whenever a device tries to connect, the system checks its IP address against the whitelist. If the IP matches one of the trusted entries, access is granted.
Step 4. Monitoring and Managing the Whitelist: New users or devices may need access, while some IPs may require removal.
a. Static vs. Dynamic IP Whitelisting
There are two types of IP whitelisting: static and dynamic.
Static IP Whitelisting: This involves adding specific IP addresses to the whitelist that don’t change over time. For example, corporate office networks often use static IPs. Static IP whitelisting is easy to implement but may present challenges for users with dynamic IPs.
Dynamic IP Whitelisting: In dynamic IP whitelisting, addresses are frequently updated to account for user IP changes. Configuring the whitelist to include IP address ranges or using a Virtual Private Network (VPN) to provide a consistent IP can be beneficial.
b. Tools and Software for IP Whitelisting
Many platforms and services provide built-in options for configuring IP whitelists:
- Cloud Service Providers offer IP whitelisting features to secure access to virtual machines, databases, or APIs.
- Web Hosting Services enable website owners to limit access to admin dashboards or databases using IP whitelisting.
- Firewalls (both hardware and software-based) allow administrators to define whitelist rules for network traffic.
- Proxy servers can be used to implement blanket IP whitelisting for entire networks.
c. IP Whitelisting vs. Backlisting
Whitelisting and blacklisting are two opposing security strategies. Whitelisting is more secure but restrictive, while blacklisting is broader but less protective. Both can work together for better security.
- Whitelisting allows access only to specific, trusted IP addresses. It’s strict and offers high security by limiting who can access the system.
- Blacklisting blocks known, harmful IP addresses while allowing everyone else. It’s more flexible but less secure because new or unknown threats may still get through.
3. Advantages of IP Whitelisting
| Benefit | Description |
| Enhanced Security | Restricts access to approved IP addresses, significantly reducing the chances of unauthorized access. |
| Controlled Access | Limits who can access your system, allowing only trusted users or devices to enter. |
| Cost-Effectiveness | It is an affordable security measure as it doesn’t require additional hardware or complex systems. |
| Complements Other Security Measures | Works well alongside other methods like firewalls, encryption, or 2FA, providing an extra layer of defense. |
IP whitelisting offers numerous benefits for businesses and individuals seeking to secure digital assets. From enhanced security and controlled access to cost-effective implementation, it is an excellent solution for restricting access to trusted users.
Below are several reasons why IP whitelisting is a valuable security measure:
a. Enhanced Security
The primary benefit of IP whitelisting is enhanced security. It reduces the attack surface by only permitting trusted IP addresses to access your network or application.
This means that even if someone manages to steal login credentials, they would still be blocked from accessing the system if their IP isn’t whitelisted.
This can be particularly useful for:
- Securing internal systems: Only trusted employees can access sensitive databases or networks.
- Protecting APIs: Ensuring only pre-approved users can send requests to your API prevents unauthorized usage or abuse.
- Website administration: Restricting access to sensitive areas can prevent external attacks, such as brute-force login attempts.
b. Controlled Access in Business Environments
IP whitelisting is commonly used in business settings to provide controlled access to specific resources. For instance, companies can restrict access to only the IP addresses of employees working from specific office locations or company VPNs.
Some business use cases include:
- Employee remote access: Companies can whitelist the IP addresses of remote workers or their company-issued devices.
- Third-party access: Provide access to external contractors, vendors, or partners to ensure that only they can connect to your systems.
c. Cost-Effective Security Solution
Compared to other security measures, such as sophisticated firewalls or intrusion detection systems, IP whitelisting is relatively simple and inexpensive to implement. That makes it an attractive option for small and medium-sized businesses with limited IT budgets.
While it is not a substitute for more advanced security measures, IP whitelisting can be an effective first layer of defense for protecting critical assets.
d. Complementary to Other Security Measures
IP whitelisting can be easily combined with other security measures to create a multi-layered defense strategy. For example:
- Two-factor authentication (2FA): Even if an attacker obtains login credentials, 2FA combined with IP whitelisting can prevent unauthorized access.
- VPNs or Proxy Servers: These can provide a consistent IP address for remote workers, which is then whitelisted for secure access.
- Firewalls and intrusion detection systems: Works well alongside firewalls and IDS solutions, providing another defense against unauthorized access.
Looking for a Secure Proxy Solution?
Combine the power of IP whitelisting with a high-performance proxy service. RapidSeedbox proxy servers support advanced security features and come with world-class 24/7 support.
4. How to Implement IP Whitelisting
Implementing IP whitelisting is a straightforward process but requires careful planning and management. The steps below will guide you through setting up IP whitelisting on different platforms.
a. IP Whitelisting on Web Servers
You can configure the server’s settings on a web server to restrict access based on IP addresses. For example, in Apache, you can use the .htaccess file to create whitelist rules:
|
1 2 3 4 |
<Directory "/path/to/your/directory"> Require ip 192.168.1.1 Require ip 203.0.113.0/24 </Directory> |
This configuration only allows access to the specified IP addresses or IP ranges.
b. Cloud Platforms
Cloud platforms often provide built-in security groups or firewall settings for IP whitelisting. For example, in AWS, you can create a security group and define inbound rules to allow traffic only from specific IP addresses:
- Go to the EC2 Security Group settings.
- Select Edit Inbound Rules.
- Add a new rule to allow traffic from a specific IP address or range (e.g., 203.0.113.0/24).
c. Proxy Servers
If you’re using a proxy server, you can configure IP whitelisting directly in the proxy settings. This ensures that only trusted IPs can use the proxy to access the internet or internal systems. For example, in Squid Proxy, you can add the following configuration:
|
1 2 |
acl whitelist src 192.168.1.1 http_access allow whitelist |
This will allow only the specified IP address to access the proxy.
d. Firewall Configurations
Many hardware and software firewalls allow you to create IP whitelist rules. In Cisco firewalls, for example, you can configure an access control list (ACL) to whitelist specific IP addresses:
|
1 |
access-list 100 permit ip host 192.168.1.1 any |
This command permits traffic from the whitelisted IP address.
5. Best Practices for Managing IP Whitelists
While IP whitelisting effectively enhances security by restricting access to trusted IP addresses, managing whitelists efficiently ensures they function smoothly and do not inadvertently introduce vulnerabilities.
a. Whitelisting IP Ranges
In some cases, it may be impractical to whitelist individual IP addresses, especially in environments with many users or devices. Instead, you can whitelist an IP range. For example, an entire office might share a block of IP addresses issued by the same ISP.
Whitelisting a range can be helpful in situations where:
- Multiple users work from the same physical location (e.g., a corporate office).
- An ISP dynamically assigns IPs within a specific block, allowing users to connect from different IPs within that range.
Note: When using IP ranges, it’s crucial to limit the size of the range as much as possible to avoid overexposing your systems. An extensive IP range could inadvertently allow access from unintended IPs, weakening the security of your whitelist.
b. Regular Reviews and Audits
A whitelist is only as secure as its most up-to-date entries. As users or devices are added or removed from your system over time, you must update the whitelist accordingly.
If old or irrelevant IP addresses remain on the whitelist, they could become potential entry points for attackers. Regularly auditing the whitelist ensures that only authorized and currently active IPs have access.
Steps for Effective Whitelist Audits:
- Periodic Reviews: Schedule regular reviews—monthly, quarterly, or based on your organization’s needs—to check the list of whitelisted IP addresses.
- Remove Unused IPs: Immediately remove any IPs that no longer need access, such as former employees, outdated servers, or vendors whose contracts have ended.
c. Combine With Other Security Measures
While IP whitelisting is a valuable tool, it should not be the sole security measure you rely on. Security is most effective when layered.
Combining IP whitelisting with other measures can provide more robust protection against potential attacks. Some complementary security strategies include:
- 2FA: Adds another level of protection by requiring a second form of authentication, such as a mobile verification code.
- Encryption: Ensures the data remains unreadable even if an unauthorized user gains access without the proper decryption keys.
- Intrusion Detection Systems (IDS): Can monitor for unusual activity or attacks from within whitelisted IP addresses.
d. Automate IP Whitelist Management
Several tools and platforms allow you to automate adding and removing IP addresses from the whitelist, making managing changes in real time easier. For example:
- IP Address Tracking: Use a tool to automatically detect changes in IP addresses and update the whitelist accordingly.
- Temporary Access Control: After a pre-determined period, the system can automatically revoke any granted temporary access.
- APIs and Scripts: Many cloud providers and systems offer APIs or scripts to help automate the addition and removal of IPs.
e. Document the Whitelisting Process
Clear documentation allows IT staff, administrators, and security teams to understand who has access, how IP addresses are managed, and what steps to follow when updating the whitelist.
Key Areas to Document Include:
- Whitelist Policies: Define which IPs or ranges are allowed, who can add or remove IPs, and what criteria determine whether an IP should be whitelisted.
- Access Logs: Keep logs of all whitelist changes, including the date, time, reason for change, and who authorized the change.
- Procedures for Adding and Removing IPs: Provide step-by-step instructions for adding or removing IP addresses to the whitelist, including which systems need to be updated (e.g., firewall, web server, cloud services).
6. Final Thoughts
IP whitelisting is a powerful and relatively simple tool in the network administrator’s security arsenal. However, this alone is far from enough. To maximize its effectiveness, you should combine it with other security protocols.
It’s also essential to remember that while setting up and maintaining an IP whitelist is straightforward, its effectiveness can vary. To maximize your benefits, pay close attention to management and proper configuration.
Is Your Proxy Setup Secure Enough?
RapidSeedbox proxies offer robust security and reliable service. If you’re serious about protecting sensitive information, you’ll love the seamless integration of security and performance.
0Comments