As cyber threats evolve, so does the need for tools to protect sensitive information. One such tool that plays a vital role in enhancing online security is the HTTPS proxy. It’s a proxy server with specific security functions that protect your data from prying eyes.
This article aims to provide an understanding of HTTPS proxies, primarily for business users. It includes functional knowledge of how HTTPS proxies work, their advantages and limitations, and their practical applications in a business environment.
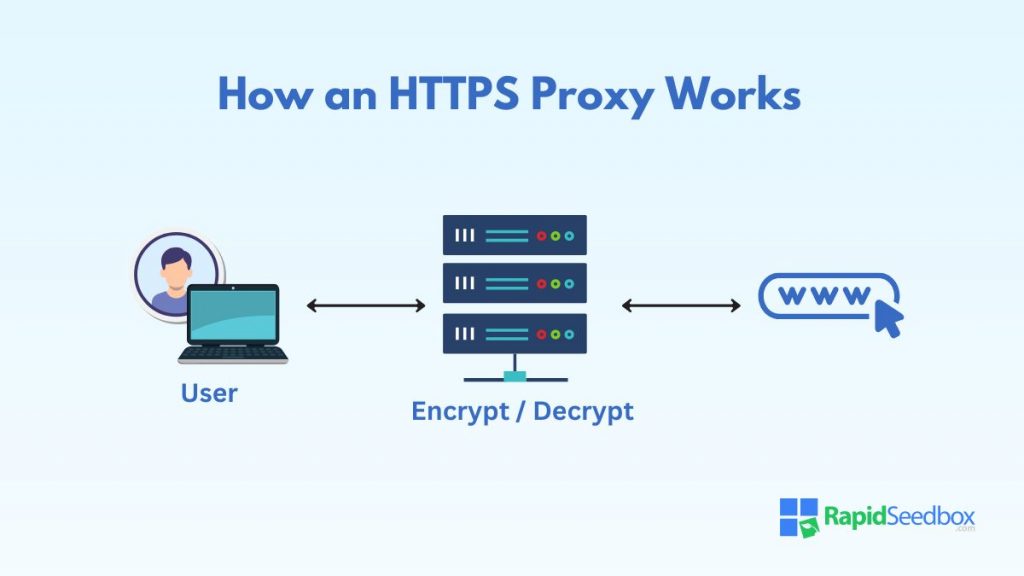
Table of Contents
- What is the Meaning of HTTPS Proxy?
- How Does HTTPS Proxy Work?
- Benefits and Limitations of HTTPS Proxy
- HTTPS Proxy Business Use Cases
- Best Ways to Implement HTTPS Proxy
- Frequently Asked Questions
- Final Thoughts
1. What is the Meaning of HTTPS Proxy?
An HTTPS proxy is a type of proxy server that explicitly handles HTTPS traffic, which is the encrypted version of the Hypertext Transfer Protocol (HTTP). In simple terms, it serves as a middleman between your devices and the websites you access.
While both HTTPS and HTTP proxies serve as intermediaries between a client and a server, the key difference lies in their security level. An HTTP proxy deals with unencrypted data, meaning anyone who intercepts it can read it easily.
2. How Does HTTPS Proxy Work?
When you attempt to access a website through your browser, it sends a request. If an HTTPS proxy is in place, this request is directed to the proxy server instead of going directly to the target website.
Once it receives the request, the proxy establishes a secure, encrypted connection between your device and the website’s server using SSL/TLS protocols. This ensures that any data exchanged remains confidential and secure.
After establishing the encrypted connection, the proxy forwards your request to the target web server. The web server processes the request and returns the response to the proxy server.
Finally, the proxy decrypts, processes, and re-encrypts the data before sending it back to the user, completing the cycle.
a. The Encryption and Decryption Process
- SSL/TLS Handshake: When you connect to a website through an HTTPS proxy, the proxy exchanges cryptographic keys to establish a secure session.
- Data Encryption: Once the connection is established, all data from your device to the target server (and vice versa) is encrypted. This encryption ensures that the data cannot be read even if it is intercepted during transmission.
- Data Decryption: Upon receiving the data from the target server, the proxy decrypts it, processes the necessary actions, and re-encrypts it before forwarding it to your device.
Note: Secure Sockets Layer (SSL) and Transport Layer Security (TLS) are cryptographic protocols designed to provide secure network communication. SSL is the predecessor of TLS, and both encrypt Internet data.
3. HTTPS Proxy Business Use Cases
While the focus with HTTPS is primarily on security, there are several notable advantages for business users. For example:
- Market Research: Helps prevent scraping bots from being blocked by target websites by rotating your IP address and masking your identity.
- Compliance and Auditability: Provide detailed logging and monitoring capabilities. This ensures that companies can maintain audit trails and demonstrate compliance with regulations like GDPR or PCI DSS.
- Secure Remote Access: Secures connections between remote workers and the company’s internal network, ensuring remote employees can work safely and efficiently from anywhere.
- Mobile Device Management: Can be integrated with MDM solutions. This helps ensure that all mobile traffic complies with the company’s policies.
Need a Reliable HTTPS Proxy Solution?
Discover how RapidSeedbox can enhance online security with robust HTTPS proxy services. Whether protecting sensitive business data or ensuring secure browsing, RapidSeedbox offers reliable, high-speed proxies tailored to your needs.
Start using RapidSeedbox today!
4. Benefits and Limitations of an HTTPS Proxy
HTTPS proxies offer a range of advantages that enhance online security and privacy, making them valuable tools for individual users and businesses. However, like any technology, they also come with certain limitations.
a. Benefits
- Enhanced Security: One of the primary benefits is its enhanced security. HTTPS proxies protect sensitive information by encrypting data through SSL/TLS protocols.
- Anonymity and Privacy: Help users maintain anonymity online by masking their IP addresses. When a user connects to a website through an HTTPS proxy, the website only sees the proxy’s IP address.
- Access Control and Filtering: Businesses often use HTTPS proxies to control access to certain websites or online content. They do this by setting rules on what can be accessed through the proxy.
- Data Compression: Some proxies offer data compression features, which can reduce the amount of data transmitted over the network and speed up website load times.
- Bypassing Geo-Restrictions: You can bypass geo-blocks and access region-specific content by routing traffic through a proxy server in a different region.
b. Limitations
- Complexity in Configuration: Setting up and configuring an HTTPS proxy can be complex. Proper configuration is essential so smaller organizations may turn to a reputable third-party proxy service provider.
- Incompatibility with Certain Websites: Some websites, particularly those with strict SSL/TLS settings, may not function properly when accessed through an HTTPS proxy.
- Cost Considerations: While free HTTPS proxy services are available, they often have limitations in terms of speed, bandwidth, and reliability.
5. Best Ways to Implement HTTPS Proxy
Implementing an HTTPS proxy effectively requires careful planning and consideration of various factors. Whether setting up for the first time or optimizing an existing setup, following best practices can help you maximize its benefits.
a. Choosing the Right HTTPS Proxy Service
- Security Features: Prioritize service providers that offer robust security features. Look for services that provide strong SSL/TLS encryption, support for modern cipher suites, and additional security measures like malware filtering or intrusion detection.
- Performance and Reliability: Consider services that provide load balancing, which can distribute traffic across multiple servers to optimize speed and efficiency.
- Scalability: Choose a service that can scale with your business needs. As your organization grows, the proxy service should be able to handle increased traffic without compromising performance or security.
- Ease of Use: A service with a simple, intuitive interface will reduce the learning curve and make it easier for your IT team to manage.
b. Implementation Steps
- Assess Your Network Requirements: Before implementing the proxy, consider the number of users, types of applications, and security requirements your network must handle.
- Select Appropriate Hardware/Software: This could range from dedicated proxy appliances for large enterprises to cloud-based services or software proxies for smaller businesses.
- Configure Proxy Settings: Configure proxy settings such as IP whitelisting, traffic filtering rules, and SSL/TLS certificate management. Ensure the proxy is correctly positioned within your network, typically between your firewall and internal network.
6. Frequently Asked Questions about HTTPS Proxy
An HTTPS proxy only routes specific browser traffic and encrypts data using SSL/TLS. In contrast, a VPN encrypts all internet traffic from your device, including non-browser applications.
To enable an HTTPS proxy, you must typically configure your device’s network settings or use a browser extension. On most operating systems, you can go to the network settings and enter the proxy server’s address and port number under the proxy settings section.
You can verify if your proxy is working correctly by checking your IP address through an online IP checker tool before and after enabling the proxy. The tool should display the proxy server’s IP address instead of your own.
Free proxy services often have significant risks, including lower security standards, slower speeds, and limited features. Some free services may log your browsing activity or inject ads into the websites you visit, compromising your privacy.
You can use an HTTPS proxy for web scraping, and it’s often recommended for added security and anonymity. However, it’s crucial to comply with the target website’s terms of service to avoid potential legal issues.
7. Final Thoughts
HTTPS proxies are potent tools crucial in enhancing online security, privacy, and control over internet traffic. By encrypting data and acting as an intermediary between your device and the web, HTTPS proxies protect against various cyber threats.
Whether you’re considering using one for personal security or as part of your organization’s network strategy, understanding how they work and how to use them properly is vital to making the most of this technology.
Want to Improve Your Web Scraping Efficiency?
RapidSeedbox’s HTTPS proxies are perfect for businesses engaged in web scraping and data collection. Avoid IP bans, enhance anonymity, and ensure secure data transfer with our high-speed proxies.
0Comments