One of the most challenging things for operators like Email Service Providers (ESPs) today is combating the humble email spammer bot. These simple yet sophisticated tools swamp servers and clog inboxes worldwide.
Several solutions are already in place, but they must be more effective. This article explores the possibilities of using IPv6 in email spammer bot defense.
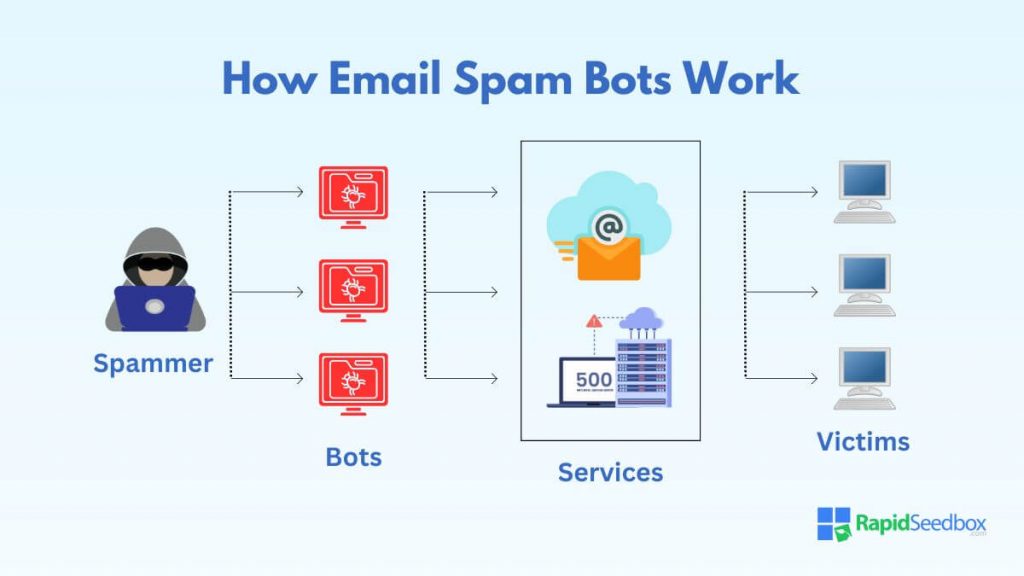
Table of Contents
- What is an Email Spammer Bot?
- How an Email Spammer Bot Works
- Overcoming an Email Spammer Bot With IPv6
- How ESPs Can Obtain IPv6 Addresses
- Migrating to IPv6 for ESPs
- Potential Challenges and Limitations of IPv6
- Final Thoughts
- Frequently Asked Questions
- References
1. What is an Email Spammer Bot?
An email spammer bot is a software designed to distribute unsolicited bulk messages, commonly known as spam, via email. These bots are often part of extensive networks known as botnets. Email spammer bots pose significant threats to consumers and email service providers.
Aside from the massive volume of unwanted emails it can produce, an email spammer bot can deliver malware. Combating these bots has been an ongoing effort by Internet Service Providers (ISPs), ESPs, security companies, and more worldwide.
However, this task isn’t easy since most email spammer bots have significant defenses. For example, they often use techniques to obscure their origin, such as spoofing email headers or rotating IP addresses.
They are also “trained” to avoid spam filter algorithms and capable of adapting to new email systems.
2. How an Email Spammer Bot Works
Most email spammer bots follow a similar modus operandi. This typically involves several key steps:
- Infection: The email spammer bot begins by infecting a computer or server. Once the device is infected, it can be controlled remotely.
- Control and Command: The infected device becomes part of a botnet and is ready for instructions on when and how to send spam.
- Gathering Email Addresses: Spammer bots typically gather email addresses by scraping websites, intercepting internet traffic, or purchasing email address lists.
- Crafting Messages: The bots generate email messages based on templates. These may include links to malicious websites or advertisements for illegitimate products.
- Distribution: Once the messages are ready, the botnet executes the command to send out spam emails to the addresses collected.
3. Overcoming an Email Spammer Bot With IPv6
IPv6 addresses several limitations of the older IPv4 system, especially in managing and mitigating email spam. The advantages range from more address space to enhanced security protocols and traceability.
The advantages are exceptionally prominent for ESPs, who can use rented IPv6 addresses to combat email spam in several ways:
Enhancing Traceability and Accountability
With each customer potentially having a unique IPv6 address, ESPs can enhance the traceability of the email flow. This aids in quickly pinpointing the origin of spam, facilitating more effective and targeted responses.
Implementation Strategy: Implement detailed logging and monitoring of each IPv6 address. Automated tools can analyze sending patterns and flag anomalies indicative of spam, such as sudden spikes in email volume or shifts in email content that diverge from typical patterns.
Leveraging IPv6’s Built-in Security Features
IPv6 inherently supports IPSec, offering encryption and authentication that are not standard in IPv4. This can secure email transmissions directly at the IP layer, adding a layer of security against man-in-the-middle attacks and eavesdropping.
Implementation Strategy: ESPs should configure their IPv6 infrastructure to utilize IPSec for all email transmissions. Training and protocols should also be developed to ensure that all network administrators are proficient in securing IPv6 connections.
Building Advanced Filtering Techniques
ESPs can use IPv6 addresses to implement more granular filtering rules. For example, different segments of the IPv6 address space can be associated with different levels of trust or risk based on historical sending patterns.
Implementation Strategy: Develop advanced filtering algorithms that consider the hierarchical structure of IPv6 addresses. By analyzing the subnet prefixes, ESPs can apply different filtering rules, adjusting the aggressiveness of the spam filtering based on reputation.
SPF and DKIM
With IPv6, ESPs can more reliably implement Sender Policy Framework (SPF) and DomainKeys Identified Mail (DKIM) due to the reduced likelihood of IP address spoofing. These technologies help verify that the domain owner authorizes the sending server.
Implementation Strategy: Encourage and assist customers in correctly setting up SPF and DKIM records for their domains.
Are You Facing Email Spammer Bot Problems?
Protect your customers by implementing IPv6 and take spam combatting efforts to whole new levels. Rent IPv6 addresses from RapidSeedbox to enjoy best-in-class support and service.
————
4. How ESPs Can Obtain IPv6 Addresses
ESPs seeking to upgrade their infrastructure to IPv6 face the critical task of obtaining IPv6 addresses. This section explores how ESPs can acquire these addresses.
Internet Service Providers
Many ISPs are equipped to provide IPv6 addresses as part of their service offerings. However, not all ISPs are equal in their IPv6 support. ESPs should select an ISP that not only offers IPv6 capabilities but also provides robust support for the transition process.
Typically, ISPs allocate a block of IPv6 addresses to customers. ESPs need to understand the size of the block (usually provided as a prefix like /32, /48, etc.) to ensure it meets their distribution needs.
Regional Internet Registries
RIRs allocate IP addresses within specific regions. ESPs can obtain IPv6 addresses directly from registries in their zone:
- North America – ARIN
- Europe – RIPE NCC
- Asia Pacific – APNIC
- Latin America and the Caribbean – LACNIC
- Africa – AFRINIC
However, this method is more complex and typically involves demonstrating the need for the IPv6 addresses and producing a utilization plan.
IPv6 Rentals from Specialized Providers
Renting IPv6 addresses is an ideal solution for ESPs that require flexibility or wish to avoid the process of direct allocation from RIRs. This method of IPv6 rental provides immediate access to IPv6 addresses without hassle.
RapidSeedbox is one of the best IPv6 address rental providers. Obtaining your IPv6 addresses here can be particularly advantageous for ESPs looking to expand their network capabilities quickly and efficiently.
This method of IPv6 rental provides immediate access to IPv6 addresses, bypassing the often lengthy and complex allocation processes involved with direct RIR engagements.
Compared to the overhead of managing a large pool of IP addresses, renting can be a cost-effective solution for ESPs, particularly those that are mid-sized or in the scaling phase.
5. Migrating to IPv6 for ESPs
Transitioning to IPv6 for ESPs typically involves enhancing network capability and security. Here’s a brief overview of the steps involved:
- Assessment and planning
- IPv6 address allocation
- Network configuration
- Implementing dual stack capabilities
- Email and application testing
I recommend reading our article “A Guide to IPv6 for Email Infrastructure” for technical details and practical tips on ensuring a smooth transition.
6. Potential Challenges and Limitations of IPv6
Transitioning to IPv6 presents numerous benefits for ESPs. However, this transition has its challenges and limitations. Understanding these potential hurdles can help ESPs prepare and strategize effectively.
- Configuration Challenges: IPv6 introduces a new addressing scheme and requires changes in network configurations. For ESPs, multiple devices to support IPv6 can be complex and prone to errors.
- Compatibility Issues: Not all network equipment and software are fully compatible with IPv6. This can lead to significant interoperability issues, requiring new hardware or software investment.
- Staff Training: IT staff often have a knowledge gap regarding IPv6 technologies. Training personnel in IPv6 configuration, troubleshooting, and security can be a significant undertaking.
- Transition Mechanisms: Dual-stack environments where IPv4 and IPv6 coexist can create security loopholes.
- More Fuel for Spammers: While IPv6’s address space is a notable advantage, it can also help spammers by giving them more IP addresses to rotate and avoid spam detection filters.
- Complexity in Management: Although the ample space of IPv6 addresses is a benefit, it also complicates managing and monitoring these addresses effectively.
7. Final Thoughts
As we move into a new era of technology, it becomes increasingly apparent that email spam remains a massive problem. Only by proactively working with new technologies like IPv6 can we combat problems like the simple but robust email spammer bot.
The investment in IPv6 is not merely a response to the depletion of IPv4 addresses but a proactive measure to bolster the defense mechanisms of ESPs against increasingly resilient cyber threats.
Are your customers complaining of email spam?
Beef up your email spam-fighting capabilities with IPv6 addresses. Use them to streamline operations, increase filtering efficiency, and leverage SPF and DKIM.
_____
8. Frequently Asked Questions
Spam emails are typically sent by individuals or organizations aiming to advertise products, spread malware, or commit identity theft. Spammers often use botnets, networks of compromised computers, to send out bulk messages to avoid detection.
In many countries, sending spam emails is illegal, especially when the emails do not comply with specific legal standards. For example, the CAN-SPAM Act establishes commercial email rules and message requirements in the United States.
Cold emailing is not illegal if it meets specific regulatory standards. These standards often include providing a straightforward way for recipients to opt out of future emails, identifying the message as an advertisement, and including a valid physical postal address of the sender.
While most major email providers offer robust spam filters, services like Gmail that use IPv6 are often noted for their particularly effective spam filtering technologies. Gmail uses advanced algorithms and machine learning to effectively detect and filter spam emails.
Fighting spam emails effectively involves using advanced spam filters provided by email services, being cautious with how and where you share your email address, and staying vigilant about the content of the emails you receive.
9. References
- Karim, A., Azam, S., Shanmugam, B., Kannoorpatti, K., & Alazab, M. (2019). A comprehensive survey for intelligent spam email detection. Ieee Access, 7, 168261-168295.
- Wang, M., & Song, L. (2021). Efficient defense strategy against spam and phishing email: An evolutionary game model. Journal of Information Security and Applications, 61, 102947.
- Sochor, T. (2020). Detection efficiency improvement in multi–component anti-spam systems. In Computer Networks: 27th International Conference, CN 2020, Gdańsk, Poland, June 23–24, 2020, Proceedings 27 (pp. 91-100). Springer International Publishing.
- Rathod, S., Mali, K., Chhajed, R., Kavthale, S., & Gutte, V. S. (2023, December). Detecting Email Spam with Precision: A Logistic Regression Approach. In 2023 International Conference on Advanced Computing & Communication Technologies (ICACCTech) (pp. 169-174). IEEE.
0Comments