Carrier-Grade NAT (CGNAT) allows ISPs to provide internet access to a large number of their customers using a limited number of public IP addresses. It is a “temporary” solution to the IPv4 address exhaustion problem, and it is expected to be fully phased out once IPv6 is widely adopted.
CGNAT has amazing benefits for ISPs. It can help them save money on public IPv4 addresses and protect their IP pools. Unfortunately, CGNAT has a handful of drawbacks that need to be considered.
In this blog post, we will discuss the basics of CGNAT, its benefits and drawbacks, and how to determine if you are using CGNAT. We will also discuss some of the alternatives and workarounds to CGNAT.

Disclaimer: This material has been developed strictly for informational purposes. It does not constitute endorsement of any activities (including illegal activities), products or services. You are solely responsible for complying with the applicable laws, including intellectual property laws, when using our services or relying on any information herein. We do not accept any liability for damage arising from the use of our services or information contained herein in any manner whatsoever, except where explicitly required by law.
Table of Contents
- IPv4 exhaustion: A problem for telecommunication carriers
- Introduction to CGNAT.
- NAT 101
- CGNAT 101
- CGNAT Benefits.
- CGNAT Drawbacks.
- CGNAT Alternatives and Workarounds.
- CGNAT Alternatives for Carriers (and ISPs).
- CGNAT “workarounds” for end-users.
- Determine whether you (as a home user) are behind a CGNAT.
- Frequently Asked Questions (FAQ)
- Final Words.
1. IPv4 exhaustion: A problem for telecommunication carriers
IPv4 is the dominant connection protocol on the Internet. There are a total of 4,294,967,296 possible IPv4 addresses— a number that seemed like plenty when IPv4 was first created in the 1980s. But the internet has grown unexpectedly massive since then.
So in spite of this growth, there have been various initiatives to save the IPv4 addresses from exhausting, such as CIDR, private addressing (RFC1918), NAT, IPv6 adoption, and more.
Although these initiatives have worked for some time, the official IPv4s are already finished. The IANA (a worldwide organization that manages IPv4 addresses) has already exhausted its IPv4 pool, so only the RIRs (Regional Internet Registries) can allocate new IPv4s. And, today, only a few RIRs still have IPv4 addressing under their pools, but they have already begun IPv4 rotating. Plus, some countries like India and China are already facing IPv4 address shortages.
To address these challenges, the long-term and only solution is a full migration to IPv6. Although IPv6 is already being used in some countries, full-scale adoption is taking a long time for various reasons.
Withholding from the full IPv6 migration and leveraging the massive available IPv4 space that good old NAT provides, the telecom carriers and service providers have started to implement a kind of double-NAT on a larger scale across their networks.
This solution is known as Carrier Grade NAT (CGNAT)
2. Introduction to CGNAT.
Carrier-Grade NAT (CGN or CG-NAT) started to be heavily used around 2014 by mobile network operators. As these operators saw the sharply increased demand for IPv4 addresses in mobile networks, they quickly resorted to double-NAT—CGNAT.
To get our heads around Carrier-Grade NAT, it is vital to go over NAT (its lower-scale version).
a. NAT 101
Note: Skip to the next section, if you already know the basics of NAT.
NAT is a networking tool that allows multiple devices on a private LAN to share a single public IP address for public communications. It serves as an intermediary that translates IP addresses and ports between private and public domains. NAT is a perfect solution to temporarily address the limited availability of IPv4s.
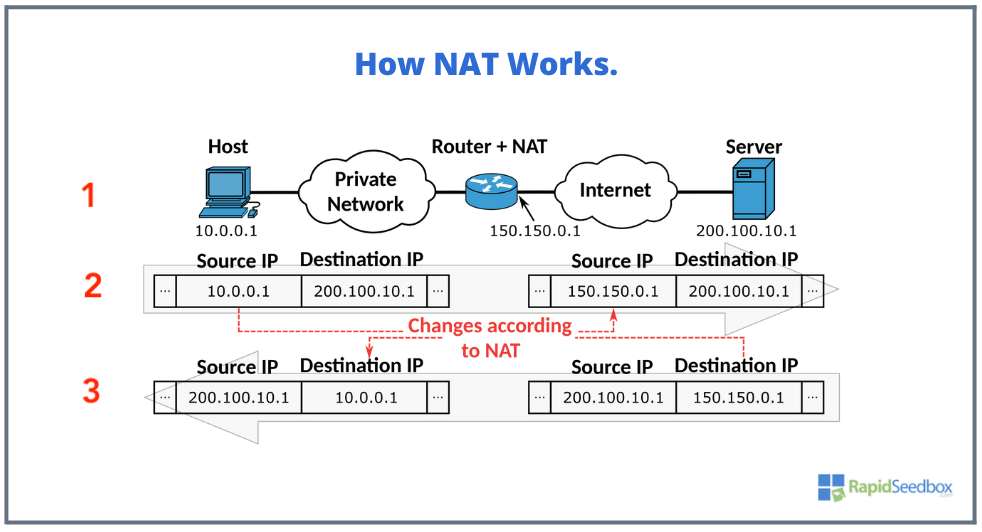
How NAT Works? Refer to the picture below.
- A “Host” with a private IP address (10.0.0.1) within a private network wants to communicate with an external “Server” on the internet with the public IP address 200.100.10.1.
- Initiate request. The “Host” initiates communication to the external “Server” via the Router + NAT which has both private and public interfaces (ports). The router’s private network interface is on the same 10.0.0.0 /8 network, while its interface is configured with a public IP (150.150.0.1). Once the Router + NAT server receives the packet, it uses the NAT protocol to map the internal/source IP 10.0.0.1 with the external/source IP (150.150.0.1) while leaving the destination IP address intact.
- Receive Response. Once the external “Server” receives the packet it responds to the router’s IP (150.150.0.1), rather than the internal 10.0.01 (because “Server” doesn’t know about the private network). Once the Router + NAT server receives the packet on its external/destination IP (150.150.0.1), it maps it again to the internal/destination IP 10.0.0.1 while leaving the source IP address intact.
A few benefits and drawbacks of NAT.
As mentioned at the beginning of this section, NAT allows having (depending on the IP address class used) thousands to millions of IPv4s for private use. NAT also has always been used on private networks (homes to small businesses) for its inherited security. Additionally, NAT also allows the network admins or customers more control and simplicity over how their internal devices access external networks.
One disadvantage of NAT for telecom carriers and service providers is the inefficiency of saving IPv4s. In order to provide internet service to all their customers they would need to assign one unique public IPv4 address to each Customer Equipment Equipment (CPE)’s external interface.
To avoid the IPv4 exhaustion problem and provide Internet to a larger population, they restore to the CGNAT solution.
b. CGNAT 101
As mentioned earlier, CGNAT is a type of IPv4 network solution that provides wide-scale NAT. In fact, it is also referred to as Massively Scalable NAT or Large-Scale NAT (LSN). Carriers use CGNAT to configure multiple communication endpoints (CPEs) with private IPv4 addresses in order to connect them to the Internet under one (or a few) shared public IPv4s.
How CGNAT Works?
CGNAT works like the traditional NAT (with a few exceptions). It follows the normal private to public translations (and vice-versa), but the biggest difference is that CGNAT performs a double-NAT for a wider-scale number of devices.
For more clarity, let’s refer to the diagram below.
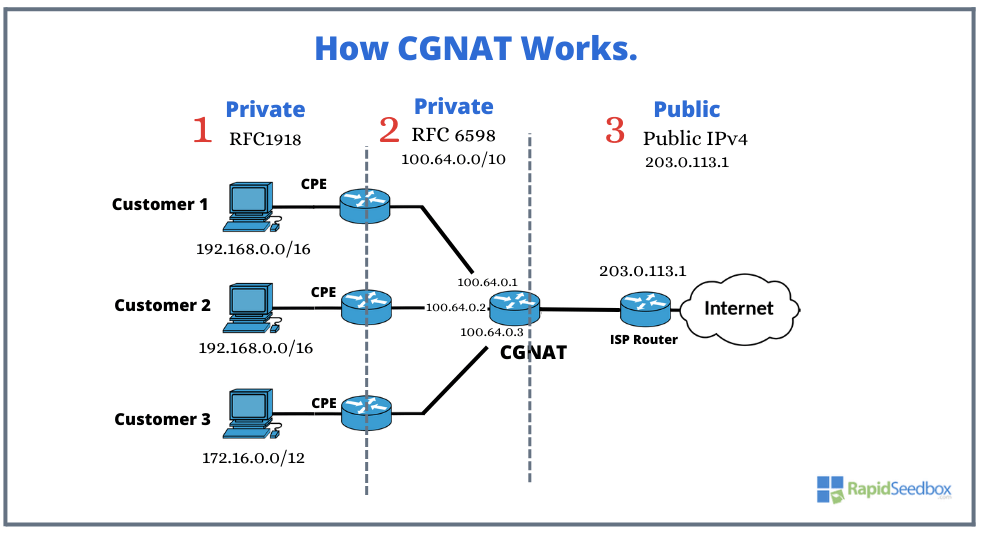
(1) Customer’s Private Network
Customer 1, Customer 2, and Customer 3 each operate their own private IPv4 networks ( RFC1918). Each customer has their unique Customer Premises Equipment (CPE) at home, which performs the first NAT. This NAT process involves translating the RFC1918 private IP addresses of the customers to a reserved IP address space designated for carrier-grade NAT (CGN). Within the private network, each user’s CPE is assigned a unique port number known as a port assignment. This port assignment aids in distinguishing between different users who share the same public IP address and helps manage their individual communications.
(2) Provider’s Private Network: CGNAT in action!
The CPE forwards the outgoing traffic to the ISP’s network, where the CGNAT server is. The CGNAT performs the second NAT using the reserved IP address space (RFC6598) 100.64.0.0/10. It replaces the private source IP and port of the outgoing traffic with a public IP and port from its pool. In addition, to ensure that multiple users sharing the same public IP address can have their traffic properly identified and routed, CGNAT assigns a unique port number to each CPE.
Note 1: The service provider’s network uses the “100.64.0.0/10” block (assigned by the IANA in 2012). This block is reserved explicitly for CGNAT scenarios and is not intended to be globally routable on the public internet and neither for private networks. It is instead, purely intended for use within the service provider’s infrastructure. The block minimizes IP address conflicts and helps in the transition to IPv6.
Note 2: It is important to note that CGNAT is stateful. This means the CGNAT router maintains a mapping table with the state information on each connection along with translations between private and public IP addresses.
(3) Public IP addresses.
The provider’s private network (RFC6598 or 100.64.0.0/10) gets translated into the public address 203.0.113.1. This way multiple customers share this IP or a limited number of public IP addresses. In this example, the public address 203.0.113.1 is an address used for illustration and documentation purposes.
3. CGNAT Benefits.
The CGNAT emerged as a solution to the painful exhaustion of IPv4s. Although CGNAT can by itself be a great advantage to telecom carriers and ISPs (while they embrace IPv6), it does not present a long-term solution.
a. Addressing IPv4 Scarcity.
CGNAT is an innovative solution to tackle the challenge of IPv4 address scarcity. The idea behind this solution lies in its capacity to allow multiple users (not from a single residency or building, but for entire regions) to share a smaller set of public addresses. With this solution, ISPs and carriers have more scalability. They can accommodate more customers using a smaller set of public IPs. CGNAT is a temporary fix while the world slowly transitions to IPv6.
b. Enhanced Security
Just like NAT, CGNAT brings an additional layer of security to the Internet connection. Since it converts private IPs into public ones, it strengthens the security of both your connection and router. It isolates the internal network devices and acts as a deterrent against unauthorized access from external entities. It safeguards customers’ devices against potential attacks that could target a specific public IP address.
c. Eases network management.
CGNAT simplifies the management of network addressing and allocation for an ISP’s private network. The single CGNAT handles the translation of customers’ private addresses to a smaller pool of public IPs. Additionally, CGNAT centralizes the management of address assignments. It reduces the complexities of managing individual public IPs for each customer.
4. CGNAT Drawbacks.
CGNAT has its significant share of drawbacks, especially for the end-user— the customer.
a. Customer’s network security and reliability concerns.
Similar to other forms of NAT, CGNAT disrupts the end-to-end communication principle. This challenge grapples with issues related to security and reliability. The shared environment that CGNAT provides means that multiple users and devices use the same public IP address for Internet communications. Although on the one hand, CGNAT creates a kind of smokescreen for attackers targeting specific devices inside the network, on the downside, it extends the attack surface. So if an attacker targets one device on that internal network, the attack could impact all the others sharing the same IP. In addition, the shared IP address can also lead to the “reputation-damaging” of other customers sharing the IP address. It could lead to being “unfairly” blocked or restricted from websites if another user sharing the same IP has been banned. If you have been unfairly banned, learn how to fix the “my IP has been banned” error.
b. Challenges for devices, apps, or services that depend on direct Internet communication.
Again, CGNAT breaks the end-to-end communication for home-device to internet-based services. It restricts the customer’s ability to access their home network from external sources. Since CGNAT adds a new intermediary layer, it affects any direct internet connections. Customers behind a CGNAT connection can expect problems with devices, apps, or services that rely on a direct Internet connection.
With CGNAT, customers usually do not have the autonomy to perform tasks like port forwarding or peer-to-peer connections. Their CPE is literally a managed virtual router under the operator’s control. Without port forwarding and peer-to-peer (with public IP) customers will have difficulties setting up home-based servers like web hosting, online gaming, video streaming, and VoIP services. In addition, customers cannot easily integrate their various Internet-connected devices like the Internet of Things (IoT) within a home environment (such as home automation).
c. Monitoring, Investigating, and Tracing Internet Access and Activities
The implementation of CGNAT can also lead to more complexities in the way telecom carriers and ISPs measure, monitor, and log access. This problem can subsequently impede effective criminal investigations and the monitoring of suspicious activities. Without a way to log, track and record private communications linked to a public IP (identification), law enforcement agencies will have difficulties tracking down criminal activity. Anyone using a shared IPv4 public IP could literally perform cybercrime actions like online fraud, illegal content distribution, cyberbullying, spamming, and more. Still, although it can be challenging to trace back connections in a double NAT scenario, it is still possible with the cooperation of ISPs (by the correlation of IP addresses and timestamps).
d. Latency Challenges.
One of the most significant challenges posed by CG-NAT is the issue of latency. This inevitable time delay has a detrimental effect on user experiences, especially with those users depending on real-time apps like online gaming, live streams, or video conferencing. Having an extra layer of network processing—the CGNAT that performs an extra NAT and routes traffic through a shred public IP, inevitably introduces added time. Unfortunately, CG-NAT deployments cause frustration among ISP’s customers, especially online gamers.
5. CGNAT Alternatives and Workarounds.
a. CGNAT Alternatives for Carriers (and ISPs).
Although operators could continue expanding their IPv4 addressing plan, reusing IPv4s, or simply expanding their CGNAT domain, the real best alternative to CGNAT (on an operator or carrier level) is IPv6. This IP version 6, will undoubtedly deal with the infamous problem of IPv4 exhaustion. It will provide internet access to a large number of users and make NAT and CGNAT disappear for good. However, IPv6 is taking a long time to fully embrace and transition (learn the reasons why and the benefits of migrating to IPv6).
b. CGNAT “workarounds” for end-users.
How to get around CGNAT? On the home-user level, there are many CGNAT alternatives that home users can use, not necessarily to bypass CGNAT (as this intermediary provides access to the internet) but to expose their home network to the internet. The only exception to this (which is not a workaround but a solution) is to get a static IP address.
- Get a static IP
- VPN
- SSH Tunnel
- SOCK5 Proxy
- TOR
- Dynamic DNS
| Workaround | Description | Advantages | Limitations |
| Static IP | Get a static IP address from your ISP. | Direct access, suitable for hosting services | Requires configuration; does not eliminate the need for CGNAT. |
| VPN | A secure tunnel that encrypts and routes traffic through a remote server, bypassing CGNAT. | Provides privacy and security; conceals real IP address. | May introduce some latency; requires a reliable VPN service. |
| SSH Tunnel | Uses SSH to create a tunnel between your computer and a remote server, allowing access with real IP. | Provides direct access to the internet; secure connection. | Requires technical knowledge; may not support all applications. |
| SOCKS5 Proxy | Routes traffic through a proxy server, masking the real IP address. | Easy to set up; can be used for specific applications. | Limited to proxy-supported applications. |
| TOR | Routes traffic through a network of relays to anonymize your connection and bypass some restrictions. | Anonymity, potential to access blocked content | Performance impact, not all websites are TOR-friendly. |
| Dynamic DNS | Updates DNS records to reflect changing IP addresses, helpful for hosting resources. | Useful for hosting services; works around some CGNAT limitations. | Requires configuration; does not eliminate need for CGNAT. |
6. How to Determine Whether you (as a Home User) Sit Behind a CGNAT.
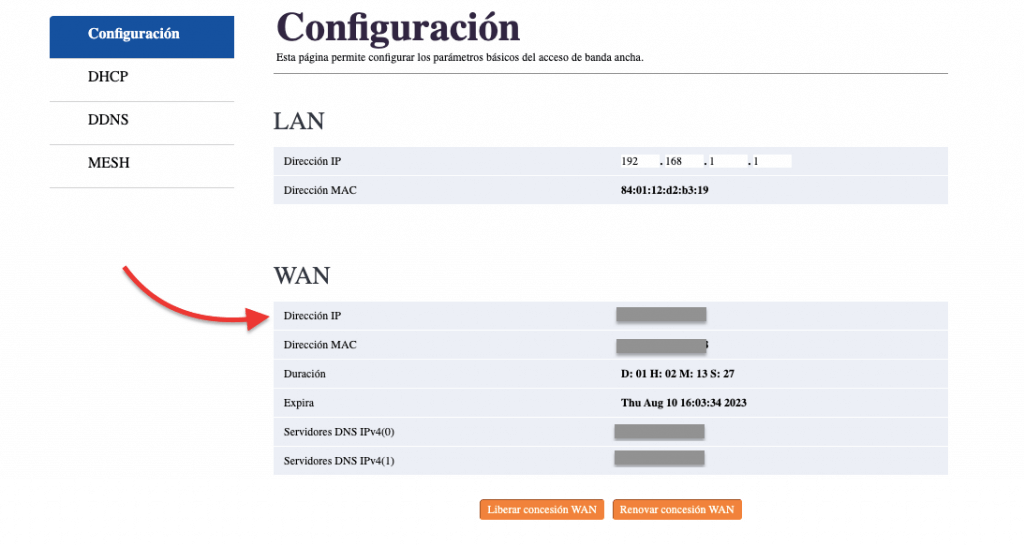
a. Check your router’s WAN IP address.
If your router’s WAN IP address is in the range of 100.64.0.0/10, then you are most likely behind CGNAT. As mentioned before, this range of IP addresses is reserved for CGNAT use.
- To check your WAN log into your home router’s interface. This can be done by entering the router’s IP address (something like 192.168.0.1 or 192.168.1.1) in your web browser.
- Once logged in, check around for the router’s status page and find your WAN IP address.
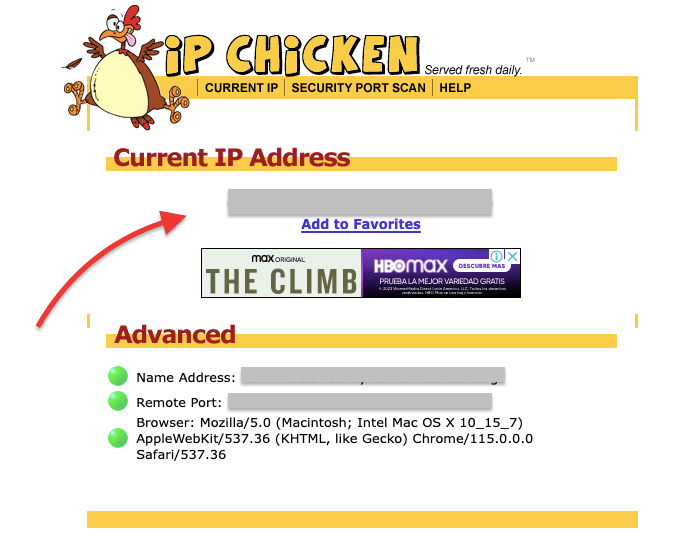
b. Use an online tool to check your public IP address.
There are many free public IP lookup sites like Whatismyip, Whatismyipaddress, or IPChicken that you can use to check your public IP address.
- If the IP address you get is different from the IP address of your router’s WAN interface, then you are most likely behind CGNAT.
- If the IP address you see here, matches the IP address assigned to your router’s WAN interface, then you might not be behind a CGNAT.
c. Use the traceroute tool.
Run a traceroute to your public IP address. The traceroute is a network utility tool built in all common OSs. It can be used to see the path that your traffic takes to reach its destination. If the traceroute shows two or more hops with repeated private IP to your public IP address, then you are most likely behind CGNAT.
Let’s simulate a traceroute (without CGNAT).
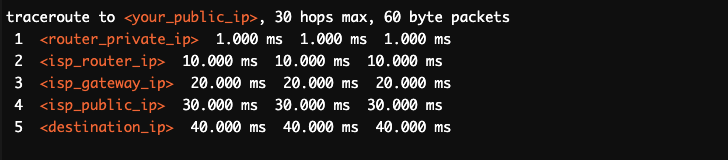
- In the previous example, there are no repeated private IP addresses. And the clear progression can be seen, from the router’s private IP to your ISP’s router IP (2), then to your ISP’s gateway IP (3), and finally to your ISP’s public IP before reaching the destination IP. This pattern would suggest that there are no intermediate CGNAT gateways in the path.
Let’s simulate a traceroute (with CGNAT).
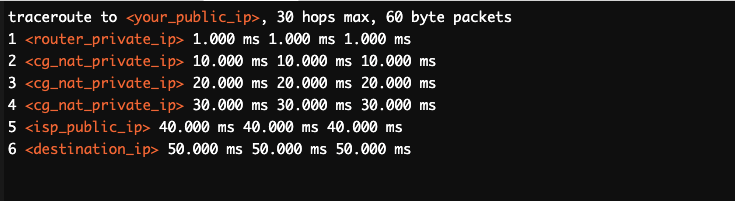
- In this example, the repeated private IP address in hops 2, 3, and 4 can indicate that your traffic is being routed through a series of internal CGNAT gateways before reaching the ISP’s public IP. The repeated private IP address suggests that your traffic is passing through multiple layers of CGNAT before it reaches the internet.
Real-life traceroute results when tracing our own public IP.
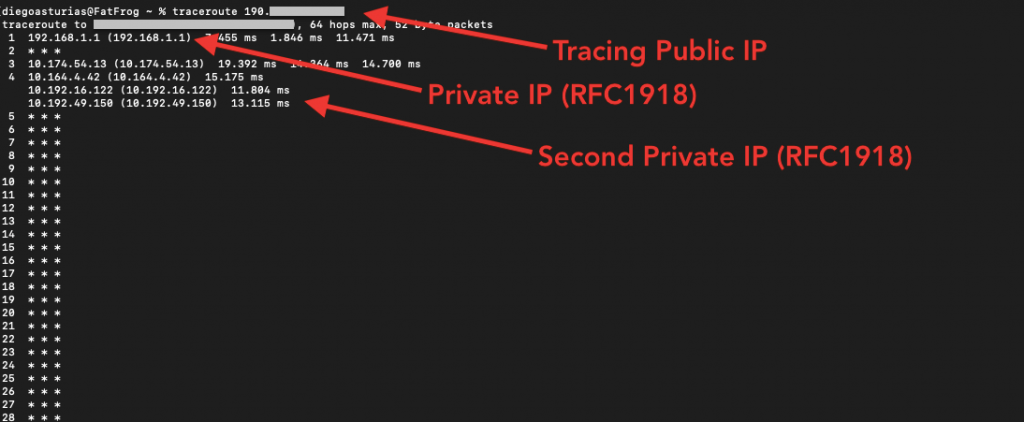
- The first hop (192.168.1.1) is the local router’s private IP address (RFC1918).
- The second hop, two (*) did not respond to the traceroute request (likely due to firewall or ICMP filtering). This hop might be the router’s interface WAN IP, an intermediary device, or any other ISP or CGNAT infrastructure.
- The following hops 3 and 4, show the existence of a class A private network. These two private IP addresses are likely to be internal routing points (within the same network as the WAN IP) within the ISP network.
From the traceroute result, we could conclude that the traffic is traversing the ISP’s internal network before reaching the public IP (interface). This is completely normal in ISP network setups and the ongoing private IP address does not necessarily indicate the presence of a CGNAT.
7. Frequently Asked Questions (FAQ)
a. Why would telecom carriers, operators, or ISPs adopt CGNAT?
The adoption of CGNAT is strongly bounded to the scarcity of IPv4 addresses. Due to the increased demand for IPv4 devices such as mobiles, carriers had to adopt NAT on a larger scale. They employed a double-NAT or CGNAT to not precisely save themselves some IPv4 space but to continue offering connectivity to more devices despite the limitation of IPv4 addresses.
b. What are some popular scenarios involving CGNAT?
The operator can use CGNAT for the common use of IPv4 address sharing (in fixed carrier or mobile networks), or also for dual-stack lite (or transition to IPv6).
c. How to set up CGNAT?
CGNAT implementation is a carrier or ISP-level task (outside the scope of this guide). But generally, to set up CGNAT, carriers would need the proper hardware (router, switch, or server), software solution, and a robust network infrastructure to accommodate multiple users. Configuring CGNAT (similar to NAT), requires port mappings, session tracking, and address assignment policies (such as allocating a pool of IPs).
d. What is NAT444?
Is a type of network architecture designed to address the challenges posed by IPv4 address scarcity and the transition to IPv6. It involves the use of two Network Address and Port Translators (NAPTs) along with three types of IPv4 address blocks to facilitate communication between devices in different networks. With NAT4444 network traffic undergoes NAT three times before reaching its destination.
e. What is NAT64, and why is relevant to CGNAT?
NAT64 facilitates the communication between IPv6-only and IPv4-only networks. It allows an IPv6-only device to communicate with an IPv4-only server by NAT, translating IPv6 packets to IPv4 and vice versa. This is particularly relevant in the context of CGNAT when an ISP’s network predominantly uses IPv6 but needs to provide access to IPv4 resources.
f. How effective can be a VPN as a CGNAT workaround?
Overall, a VPN can be an effective CGNAT workaround solution. As long as you choose a reliable and trustworthy VPN service, a VPN should bypass the CGNAT. However it’s always vital to consider your specific needs, such as speed requirements, privacy concerns, and the ability to bypass CGNAT, before deciding which VPN to use as a workaround.
g. How to perform port forwarding behind CGNAT?
Performing port forwarding behind CGNAT can be challenging due to the limited control over the public IP address and network configuration. Some potential solutions include using UPnP if supported, utilizing port forwarding services, or considering a VPN with port forwarding capabilities to expose specific ports on your device to the internet. However, the effectiveness of these methods can vary, and they may not provide the same level of control as traditional port forwarding in a non-CGNAT environment.
8. Final words.
CGNAT is a controversial technology. There are both benefits and drawbacks to implementing it. Ultimately, the decision of whether or not to use CGNAT is up to each individual ISP. Although CGNAT can help ISPs save money on IPv4 public addressing space, there are lots of potential drawbacks for end-users that ISPs should consider.
In summary (for customers):
- If you are behind a CGNAT, you will not get your own public IP address for your home network. This can impact the performance of some applications and make it more difficult to access certain online services.
- Additionally, if you are behind a CGNAT, you may not be able to host a home server or use online gaming, VoIP, or file-sharing without lag and delay.
- Try any of the workaround solutions to bypass the CGNAT proposed in this guide. Use a VPN or proxy. Or better yet, ask your ISP about any available static IPv4 public addresses.
0Comments