Introduction
In a world of online streaming media, BitTorrent remains the most popular peer-to-peer distribution by far. BitTorrent is the No. 1 cause of upload traffic—9.7% of the data we upload comes from BitTorrent.
Though it can be used to share copyright-free content with thousands of people quickly, we can’t overlook that many people use BitTorrent to download copyrighted materials they haven’t paid for.
There’s no doubt that this is copyright infringement, and most countries have stringent laws banning piracy.
Beyond the very real risk of prosecution, using BitTorrent has several other risks you should be aware of. In this article, we’ll look at the principal risks of using BitTorrent. Furthermore, we’ll share a few ways you can minimize your exposure to them.

Disclaimer: This material has been developed strictly for informational purposes. It does not constitute endorsement of any activities (including illegal activities), products or services. You are solely responsible for complying with the applicable laws, including intellectual property laws, when using our services or relying on any information herein. We do not accept any liability for damage arising from the use of our services or information contained herein in any manner whatsoever, except where explicitly required by law.
Table of Contents
- Introduction
- Copyright Infringement Risks
- BitTorrent Is Not Private
- The Risks of Malware and Viruses
- Conclusion
Copyright Infringement Risks
There are significant differences in how countries have chosen to deal with online piracy. Most countries enforce copyright laws, and many countries have criminal penalties for copyright infringement.
Yet several countries, such as Argentina, Venezuela, and Algeria, has very limited copyright protection laws. Others, like Canada and Germany, have reduced penalties for non-commercial copyright infringement.
Criminal Penalties
Though the slogan “Piracy is Theft” is often used by copyright holders, under U.S. law, online piracy is actually considered an infringement of copyright rather than theft. This is because the original copyright holder doesn’t lose the original work when it is downloaded online. Rather, a new copy of the work is created.
- In the U.S., willful copyright infringement carries a maximum penalty of $150,000 per instance.
- The federal No Electronic Theft Act states the following. “Individuals can be criminally prosecuted even if there was no monetary profit or commercial gain made”.
- The maximum penalty is five years in prison and $250,000 in fines.
Civil Lawsuits
Many copyright holders bring lawsuits against infringers in civil court. They sue the individual downloaders directly or those who facilitate file sharing, such as the owners of torrent tracker websites.
The Recording Industry Association of America (RIAA) is an example of a trade group that has made thousands of lawsuits against individual consumers in an effort to combat online sharing. Over 16,200 people were sued in just one of its huge pushes to sue individuals. Many people chose to pay a $1,000 settlement to avoid court.
This is far from the only case. In 2010, courts ordered a Minnesota woman to pay $1.5 million in damages for downloading 24 songs. The figure was later reduced to $222,000. She was forced to declare bankruptcy.
Can You Avoid Getting Sued for Copyright Infringement?
The only way to avoid any risk of downloading copyrighted materials is not to do it at all. Though some media is copyright-free, such as the movies Night of the Living Dead (1968) and Manos: The Hand of Face (1966), it’s unreasonable to keep checking the copyright status of every file you intend to download.
Despite these risks, many people will still want to torrent files anyway. To greatly minimize your risk exposure, we’ve outlined several ways to make your torrenting more anonymous in the following sections. In particular, the use of VPNs, seedboxes, and private trackers is recommended.
BitTorrent Is Not Private
One of the reasons it’s relatively easy for such lawsuits to come about is because peer-to-peer file sharing like BitTorrent is far from anonymous by default.
When you connect to a public tracker like The Pirate Bay or 1337x to download files, you often connect with hundreds or thousands of other computers worldwide. The owners of those computers can see that someone at your computer’s location is downloading that file. People know what you’re downloading.
To illustrate this further, the website I Know What You Download records the IP addresses of computers downloading. It also publishes the data publicly.
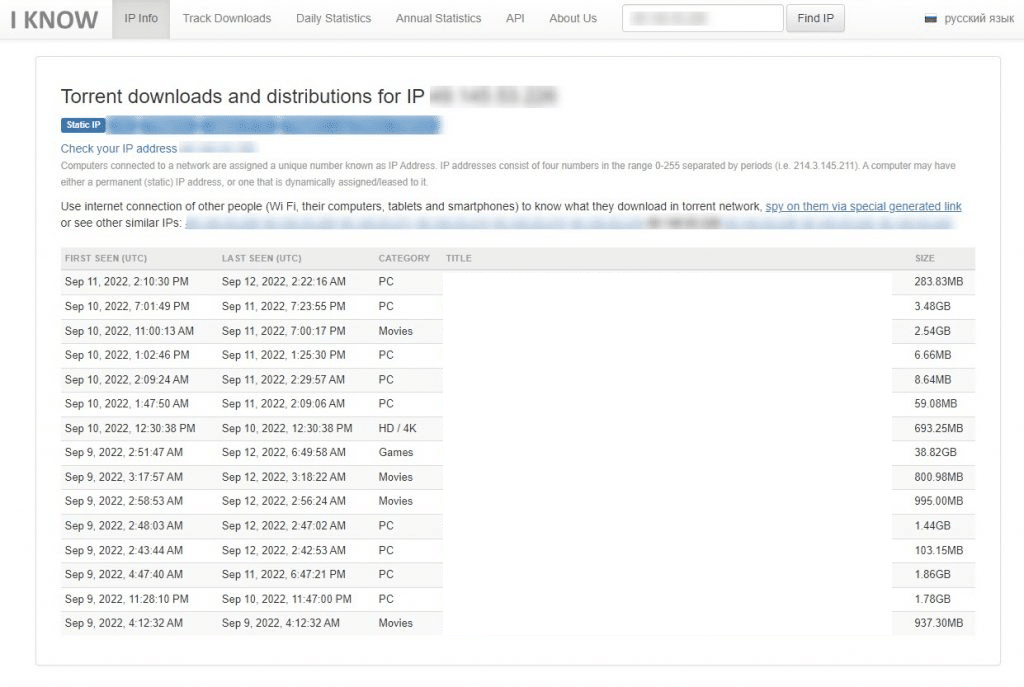
Copyright holders and trade bodies use the same process to identify which computers are downloading their copyrighted materials. They will send cease-and-desist letters, and put pressure on your internet service provider (ISP) to stop you from illegally downloading content.
As soon as anyone gets a copy of your IP address, they too could see what’s been downloaded to your computer. For instance, this can get you in trouble at work or on a college campus. And it’s been shown that governments too are tracking BitTorrent usage.
Your ISP can also easily see that you’re using BitTorrent if you don’t take additional steps to cover your tracks. Many ISPs will throttle the speed of your internet connection as soon as they detect the use of peer-to-peer file sharing, for example.
Torrent Client Encryption Settings
BitTorrent downloading programs (clients) have several settings you can use to increase your privacy and the chance that your use of BitTorrent will go undetected by your ISP. You’ll typically find these options in the Settings menu of the application. Let’s look at some of the options in the popular BitTorrent client qBittorrent.
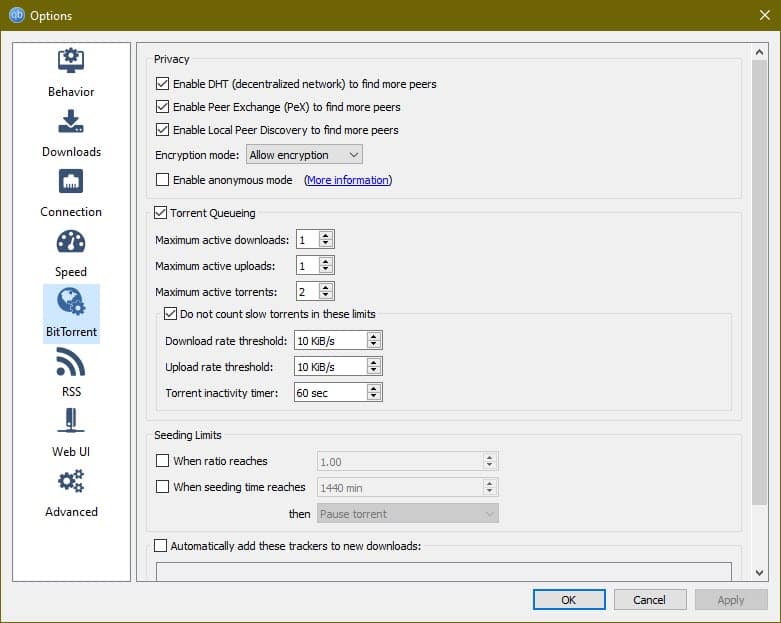
- Allow Encryption—Choosing this option will encrypt all your torrent traffic using the RC4 encryption cipher when you’re connecting to other peers that have this encryption enabled. Because it’s not enforced on all connections, this is a weak way to improve anonymity.
- Force Encryption—This mode means you will only connect to peers with RC4 encryption engaged. This means your torrents will often run more slowly because you can only connect to specific computers, but it does obfuscate your BitTorrent traffic much more. Note that while forcing encryption will usually be enough to circumvent ISP traffic shaping, it still may be possible to identify torrent traffic with 96% accuracy.
- Anonymous Mode—This mode disables many of the identifying information usually sent when torrenting, including a user agent, IP address, and BitTorrent client version. It also disables connection to peers via Local Peer Discovery and Distributed Hash Table (DHT). This improves anonymity somewhat, but some torrents won’t work because you’ll be unable to find a peer to connect to.
- IP Filtering—This feature can be used with a blocklist like Bitsurge BlockList to block connections to IP addresses known to be owned by anti-torrenting companies. Blocklists can never keep up with every IP address that should be blocked, so they’re not 100% foolproof, but it’s another level of defense you can employ.
Using Virtual Private Networking (VPN) and Proxy Services
Proxy and VPN services transmit all the data you transfer online through a proxy server. So, when you download a file through BitTorrent when using a VPN, other users will not be able to see your real IP address, making it much more difficult to track you down.
Another advantage of a VPN is the data you send is encrypted. Your government, internet service provider, and everyone else can’t see what you’re using your internet connection for. They cannot tell if the data you send is being used for BitTorrent at all; never mind snoop on the exact details of the files you’re downloading.
We cover the main differences between VPNs and proxy services in our guide: VPN vs Proxy: 6 Differences You Should Know.
Seedboxes
You can circumvent almost all risks of torrenting by using a seedbox service. A seedbox is a remote server running a BitTorrent client. All the torrenting is performed on the remote server instead of your local computer, and you administer the client through your browser.
You can download the files on your seedbox through various means, such as through your browser, FTP, or even your local BitTorrent client. Whichever method you choose, your downloading activities will almost certainly go unnoticed because you’re uploading very little data from your local computer.
Seedboxes are typically located in countries with strong privacy laws and relaxed laws on file sharing, making your torrenting activities safe.
Private Trackers
Instead of using public trackers that anyone can connect to, you can instead use private trackers that require an invite or have a stringent application process. Because of this, these private trackers aren’t so easy for anti-piracy groups to monitor, and most prefer to stick to the low-hanging fruit of public trackers.
Controlling your Network
Don’t use torrenting applications on networks you don’t control. For instance, avoid torrenting on public networks like coffee shops or internet cafes. You don’t know who else is connecting on the same network as you and whether they’re snooping on your BitTorrent usage.
Avoid using your employer or college network for torrenting. They may be monitoring the traffic being sent back and forth, and it could cause you to get into trouble or lose your job.
The Risks of Malware and Viruses
Hackers use torrenting to install viruses, trojans, and malware. They prey on users who download “cracked” games and applications. When you install cracked software, there is a chance that a malicious actor has included all manner of unwanted programs that will also be installed on your computer, often hidden away undetected. In many instances, the files you download aren’t the files you expected at all.
Malware (malicious software) comes in many forms. Viruses, for instance, are designed to spread to other computers on your network. Ransomware encrypts all your computer’s files and demands payment for their decryption. Spyware can spy on what you’re doing on your computer, sending details like bank account logins to the hacker.
Avoid Public Torrenting Sites
To limit your exposure to potentially unwanted programs, think carefully about where you download files from. Most public torrent trackers perform little to no curation of the files that are shared online, making it easy pickings for a hacker who uploads what looks like a new game that’s just come out or a sought-after, expensive application.
Reddit community Freemediaheckyeah, which has over 100,000 active users, maintains a list of public torrent sites that are considered safer to use because there is at least some moderation of content uploaded.
It also lists several private torrent sites. These sites typically require an invite and files are much more heavily moderated, so can be considered a safer location to download from.
Note that we say that downloading from these sites is safer, not safe. You’re still downloading and running files you obtained from a stranger.
Use Virus Protection
Before running any application you’ve downloaded from the internet, it makes sense for it to be scanned by a virus tool.
Windows already has good virus protection built-in that included automatic scanning, ransomware protection, and frequent threat protection updates. This is a good place to start, so ensure your Windows Security anti-virus is on.
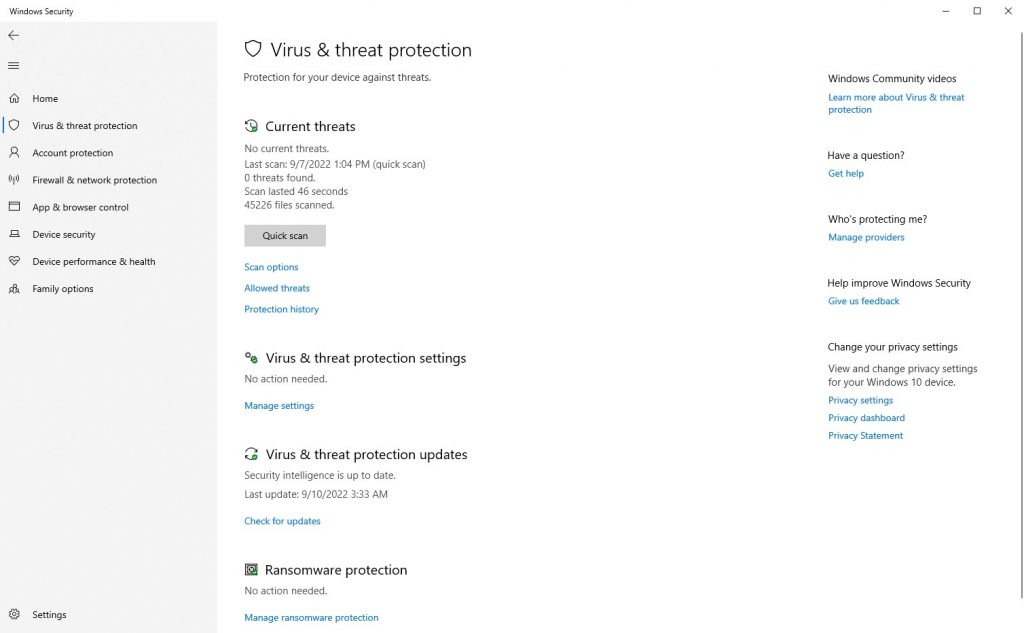
For extra coverage, you could use one or more third-party anti-virus tools. Bitdefender, Norton Antivirus, and Trend Micro Antivirus are all popular options. It’s debatable whether these solutions offer significantly better coverage than Windows Security. However, they usually come with extras such as automatic backups and support for mobile devices.
It’s a good idea to always upload any executable file (.exe) you download through torrenting to VirusTotal. This free service will scan the executable through hundreds of anti-virus software and present their results in a table. If nothing suspicious is found, the file is likely to be safe.
Conclusion
BitTorrent usage remains highly popular because it allows you to download copyrighted materials for free. Most countries have stringent laws against piracy, and there are many other risks, too.
We’ve discussed here several methods you can use to minimize the risks involved in torrenting files. Carefully consider which will work best for you so you can continue to upload and download files in peace.
0Comments